I am going through their sample app tutorial here: https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/GettingStarted.html and even though I am able to get a working app from Step 1, I consistently get warning messages about being unable to assume the Service Role I set up for this app and being unable to find permissions to check for managed updates. I already set up a service role with all the permissions listed here: https://docs.aws.amazon.com/elasticbeanstalk/latest/dg/iam-servicerole.html, and my understanding is that I should be able to get managed updates with this app.
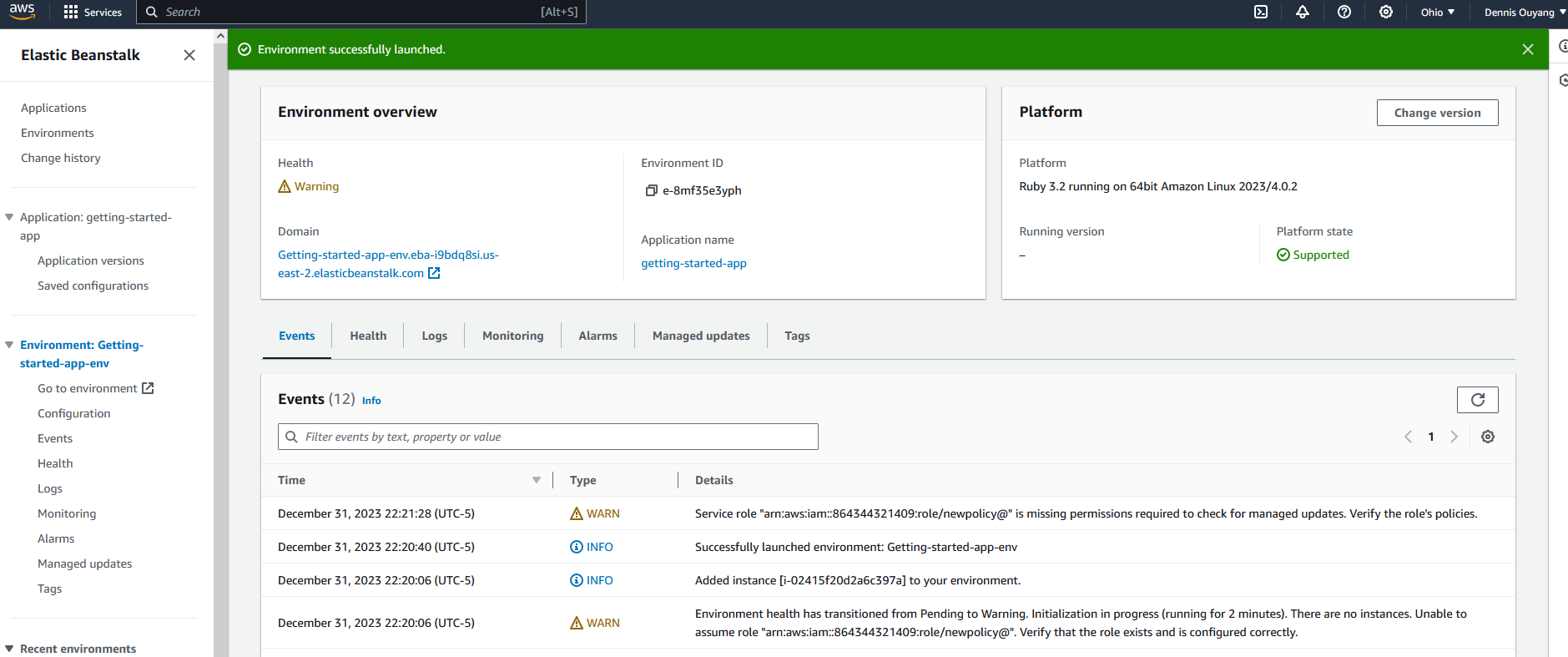
I have attached the error I am seeing on my environment page.
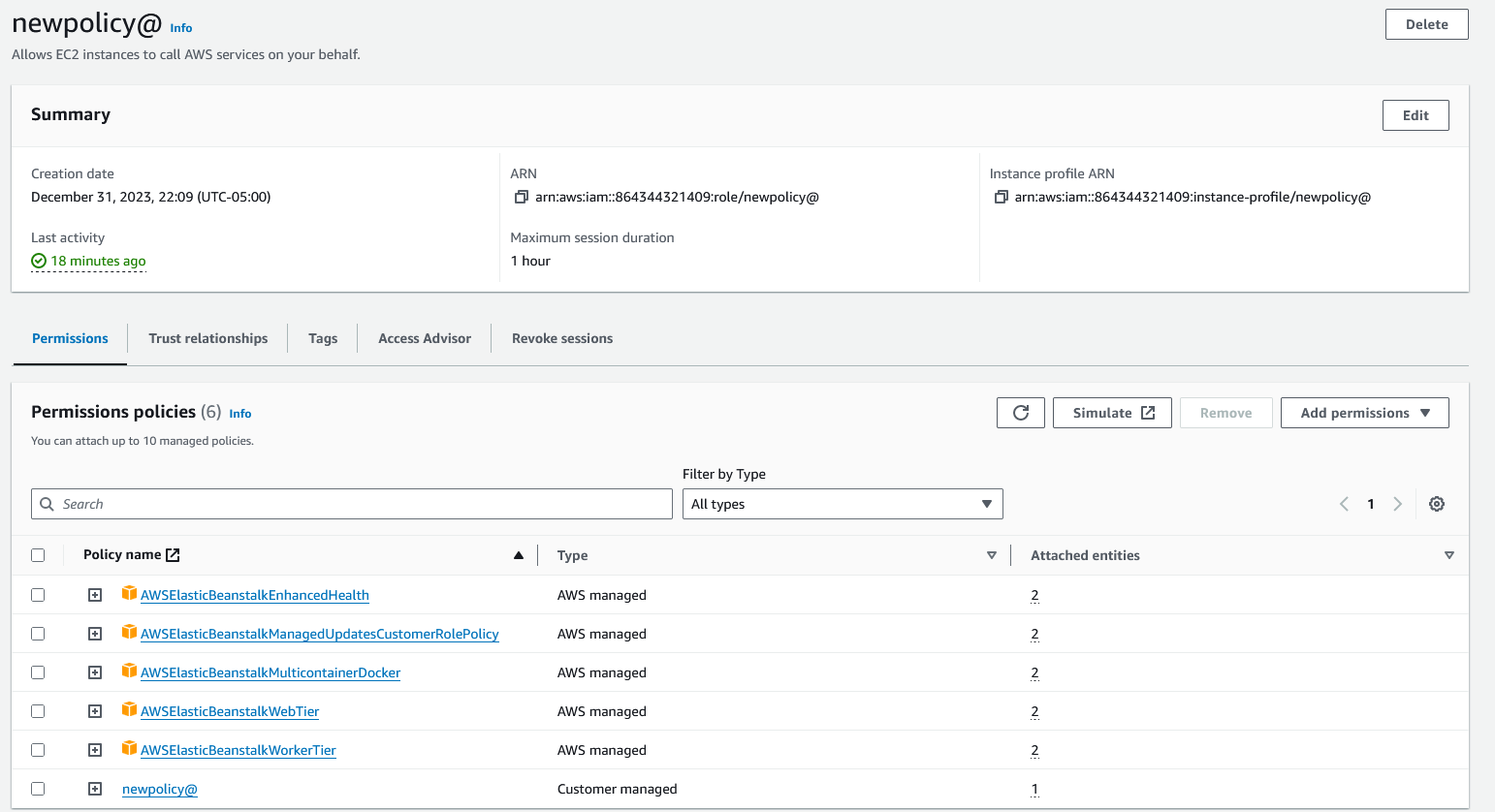
Also attaching the screenshot of what I see on my role I named newpolicy@.
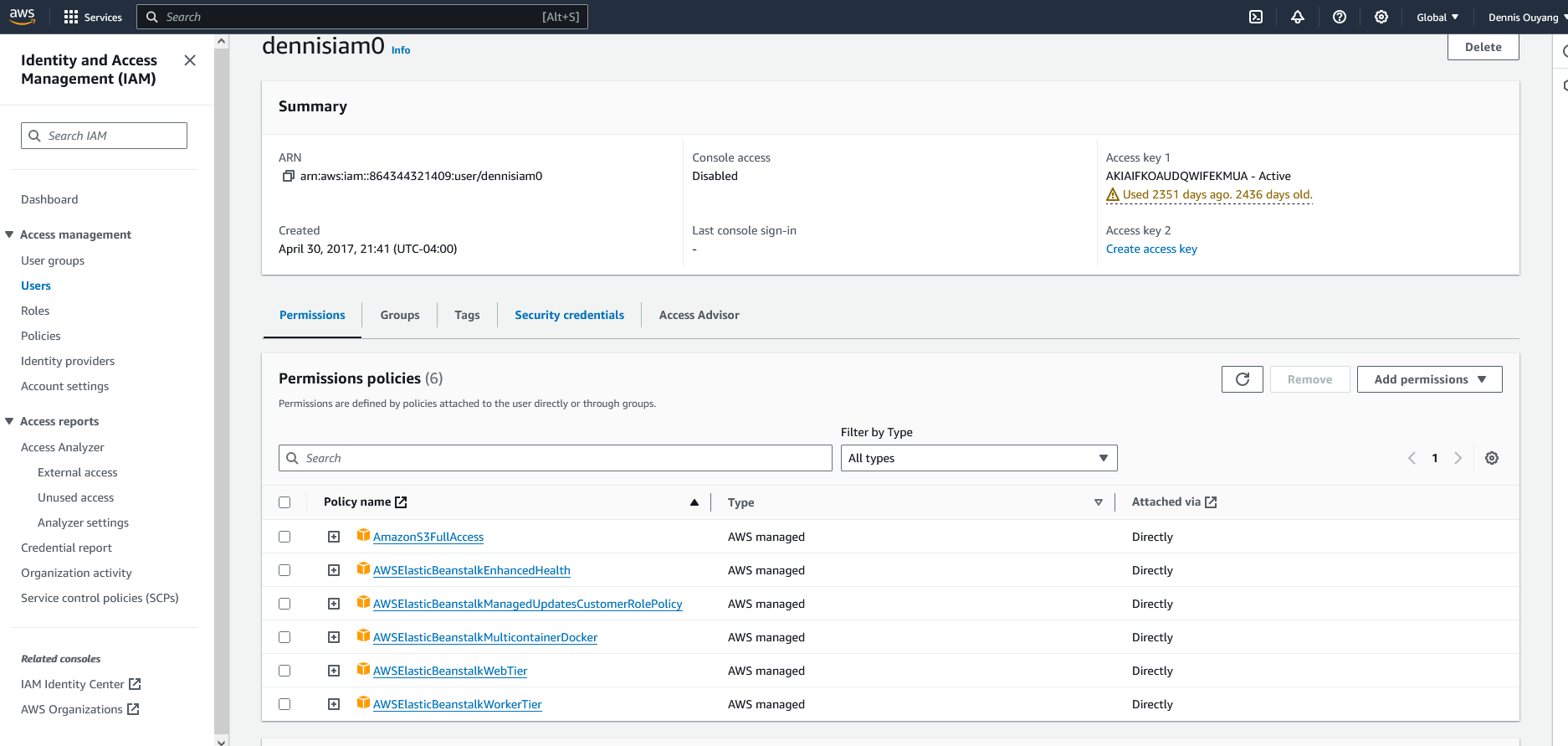
I even tried attaching the necessary policies directly to my user, which is the root user of the account.
I have deleted the app, environment, and role, and rebuilt them using the Amazon tutorials from scratch, multiple times, all with the same problem.
Tried creating a new app, with a new environment, and created a new role with added permissions including AWSElasticBeanstalkEnhancedHealth and AWSElasticBeanstalkManagedUpdatesCustomerRolePolicy along with the standard AWSElasticBeanstalkWebTier, AWSElasticBeanstalkWorkerTier, AWSElasticBeanstalkMulticontainerDocker recommended by the tutorial.
I expected to see a new app with no issues, but instead, I am getting warning events:
Unable to assume role "arn:aws:iam::xxxxxx:role/newpolicy@". Verify
that the role exists and is configured correctly.
Service role "arn:aws:iam::xxxxxx:role/newpolicy@" is missing
permissions required to check for managed updates. Verify the role’s
policies.
I can still view the sample app when I click the provided url, however.
In response to Arpit Jain’s question: here are my trust relationships for newpolicy@:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
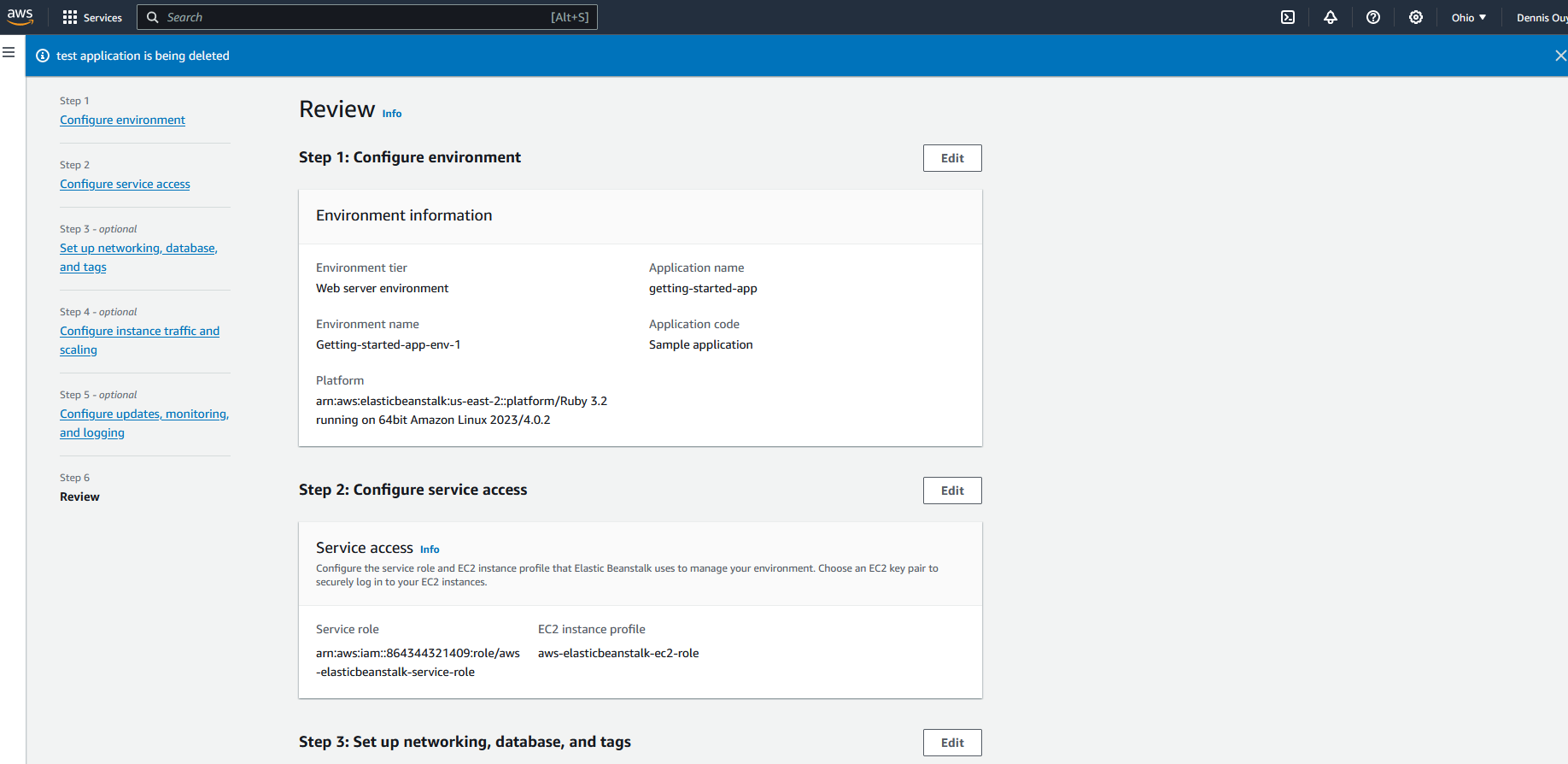
In response to Arpit Jain’s answer below, here is the profile info for my new environment:

 Question posted in
Question posted in 

2
Answers
You created a service role name –
newpolicy@for the EC2 instance but it should be created for the Elastic Beanstalk to assume the service role.Typically, Elastic Beanstalk requires two types of IAM roles: Service role and Instance profile.
Service role for Elastic Beanstalk Environment: The IAM role that Elastic Beanstalk assumes when calling other services on your behalf. When you launch an environment in the Elastic Beanstalk console or CLI, it creates a default service role that’s named
aws-elasticbeanstalk-service-role, and attaches managed policies with default permissions to this service role. If it doesn’t exist or you’d prefer to utilize a different service role, you can create it by following the instructions below. If you already have a service role, make sure you have the below-required policies. To meet the default use cases for an environment, these policies must be attached to the role of the Elastic Beanstalk service role:-In the navigation pane of the IAM console, choose Roles, and then choose Create role → Choose the AWS service role type as AWS Service → Choose the Use case as Elastic Beanstalk – Customizable → Choose Next → It should show two permission already selected –
AWSElasticBeanstalkEnhancedHealth,AWSElasticBeanstalkService(Need to addAWSElasticBeanstalkManagedUpdatesCustomerRolePolicy, will add later once the role is created) → (Optional) Set a permissions boundary → Choose Next → Enter Role name as –aws-elasticbeanstalk-service-role→ Review the role, and then choose Create role.Now from the navigation pane of the IAM console, search for the newly created Role –
aws-elasticbeanstalk-service-role→ Click on Add permissions – Attach policies → Search and selectAWSElasticBeanstalkManagedUpdatesCustomerRolePolicy→ Click Add permissions.Permissions policies for the role –
aws-elasticbeanstalk-service-role:Trust relationships for the role –
aws-elasticbeanstalk-service-role:Instance profile Role for EC2 Instances: The IAM role that’s applied to Amazon EC2 instances that are launched in your Elastic Beanstalk environment. To allow the EC2 instances in your environment to assume the required role, the instance profile must specify Amazon EC2 as a trusted entity in the trust relationship policy. Please see this answer for instructions on how to properly set it.
Hope this helps.
The tutorial is confusing. It tells the first-time user to "Use an existing service role" but doesn’t provide the opportunity to select the default aws-elasticbeanstalk-service-role. If you choose "Create and use new service role", the default service role appears. You can then move down and create an EC2 instance profile as described in the tutorial.