Current Behavior –
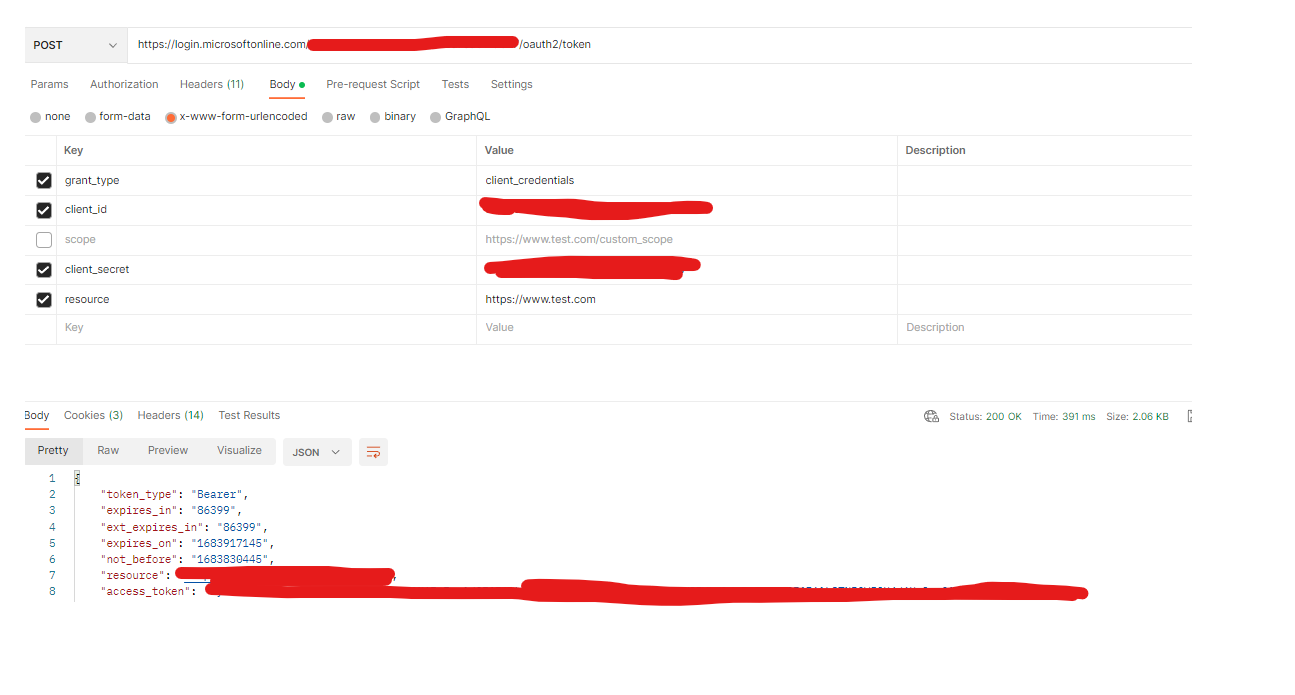
From our service-A, we are calling service-B. We are currently using client_credentials as a way to generate access_token for service-B(as shown below).
Service-B is validating token generated at their end and everything is working fine.
Expected behavior –
So, now we are looking per API based whitelisting. So, in above case service-A will be able to call all API of service-B and we want to stop that. So, looking for help to expand our current implementation to support same without changing resource (As resource means service-2 in our team).
Thus, expected behavior will be service-A can call API-1 of service-B, but not API-2.




2
Answers
In your screenshot, you are using Oauth 1.0 which you need to set
resourceand this makes you can’t set API scope inside the authorization, you need to use OAuth 2.0. By the way, client credential flow will make the scope set toxxx/.default, this flow won’t contain scope name as well, so you can’t use client credential flow as well.I have a sample here. Firstly, here’s the settings in Service-B. I integrated Azure AD into my web api project.
Then in my web api:
I used auth code flow to generate an access token which containing the scope I defined:
Then here’s my test result:
About how to expose custom API scope, you can follow this official document. This answer showed how to generate access token by auth code flow. But if you are trying to generate access token in Service-A to call Service-B, you may use on_behalf_flow, this answer contained code snippet with Microsoft identity and use _tokenAcquisition to generate access token, and this answer is for a client call AAD protected API.
I created two Azure AD Applications
ServiceAandServiceB.In
ServiceBapplication, I created sample App roles like below:In
ServiceAapplication, I added required permissions like below:Now, I generated access token by using below parameters:
When I decoded the token in the roles claim only the
api.readandapi2.readis present notapi3.read.This is the possible workaround which can be implemented to achieve your scenario. The App roles can be assigned to Users, groups or Service Principals.
Reference:
Add app roles and get them from a token – Microsoft Entra