Upon terraform I did:
resource "aws_lb" "test_lb" {
name = "test-lb-tf"
internal = false
load_balancer_type = "application"
security_groups = [aws_security_group.lb_sg.id]
enable_deletion_protection = true
access_logs {
bucket = "logs.example.com"
prefix = "test-lb"
enabled = true
}
}
#Test 1
resource "aws_route53_record" "test_staging_domain" {
zone_id = "Z09006193JFJXM3FAWH9I"
name = "myapp.example.com"
type = "CNAME"
ttl = 300
records = [aws_lb.test_lb.dns_name]
}
resource "aws_instance" "test_staging" {
ami="ami-09d64f47c232fb430"
instance_type="t3a.micro"
key_name = "common_ssh"
count=2
root_block_device {
volume_size = 30
volume_type = "gp3"
}
vpc_security_group_ids=[
"sg-0304ce47e789c538a"
]
}
resource "aws_lb_target_group" "test_staging_tg" {
name = "test_staging_tg"
port = 80
protocol = "HTTP"
target_type="instance"
}
resource "aws_lb_target_group_attachment" "test_staging-target-group-attachment" {
target_group_arn = aws_lb_target_group.test_staging_lb_listener.arn
target_id = aws_instance.test_staging.arn
}
resource "aws_lb_listener" "test_staging_lb_listener" {
load_balancer_arn = aws_lb.test_lb.arn
port = 443
protocol = "HTTPS"
certificate_arn = "arn:aws:acm:eu-west-1:962331388720:certificate/1cdd1f8c-64d5-4984-a985-133fbe0df5b0"
alpn_policy = "HTTP2Preferred"
default_action {
type = "forward"
forward {
target_group {
arn = aws_lb_target_group.test_staging_tg.arn
}
}
}
}
#Test 2
resource "aws_route53_record" "test2_staging_domain" {
zone_id = "Z09006193JFJXM3FAWH9I"
name = "myapp2.example.com"
type = "CNAME"
ttl = 300
records = [aws_lb.test_lb.dns_name]
}
resource "aws_instance" "test2_staging" {
ami="ami-09d64f47c232fb430"
instance_type="t3a.micro"
key_name = "common_ssh"
count=2
root_block_device {
volume_size = 30
volume_type = "gp3"
}
vpc_security_group_ids=[
"sg-0304ce47e789c538a"
]
}
resource "aws_lb_target_group" "test2_staging_tg" {
name = "test_staging_tg"
port = 80
protocol = "HTTP"
target_type="instance"
}
resource "aws_lb_target_group_attachment" "test2_staging-target-group-attachment" {
target_group_arn = aws_lb_target_group.test2_staging_lb_listener.arn
target_id = aws_instance.test2_staging.arn
}
resource "aws_lb_listener" "test2_staging_lb_listener" {
load_balancer_arn = aws_lb.test_lb.arn
port = 443
protocol = "HTTPS"
certificate_arn = "arn:aws:acm:eu-west-1:962331388720:certificate/1cdd1f8c-64d5-4984-a985-133fbe0df5b0"
alpn_policy = "HTTP2Preferred"
default_action {
type = "forward"
forward {
target_group {
arn = aws_lb_target_group.test2_staging_tg.arn
}
}
}
}
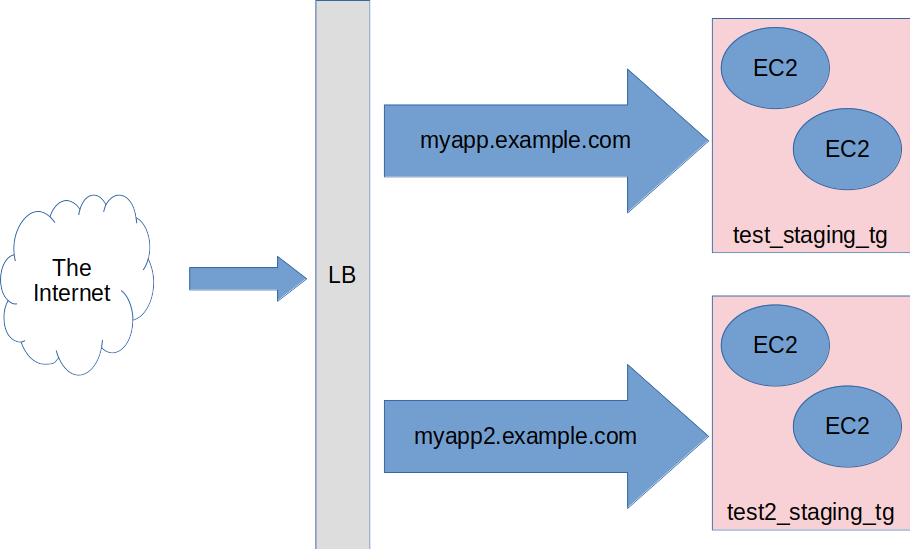
With this I try to achieve is the following:
Using a Load balancer I want to direct the approrpiate traffic into specific target group:
- The target group
test_staging_tgwill handle requests formyapp.example.com - The target group
test2_staging_tgwill handle requests formyapp2.example.com
But how I can do using terraform and hcl to sopeciufy the nessesary domain in me target groups?




2
Answers
Indeed at previous year (2023) I could define multiple domains upon aws load balancer. But recently I noticed that application load balancers do not allow for defining multiple domains as used to.
The only way to achieve this is:
For the first one you can split the terraform definition into 2 files:
test.tfAnd
test2.tf:As you can see there are 2 Load balancer rewwsources (thus 2 load balancers as well):
test_lbtest2_lbResolving its own domain respectively.
You would define multiple load balancer listener rules, one for each domain, with the
conditionbeinghost_headerthat matches the domain, and theactionbeing the target group that you want to handle that domain’s traffic.