I’ve been trying to get a db connection working in my lambda and having the worst time retrieving my password from secrets manager.
When I run the lambda I get
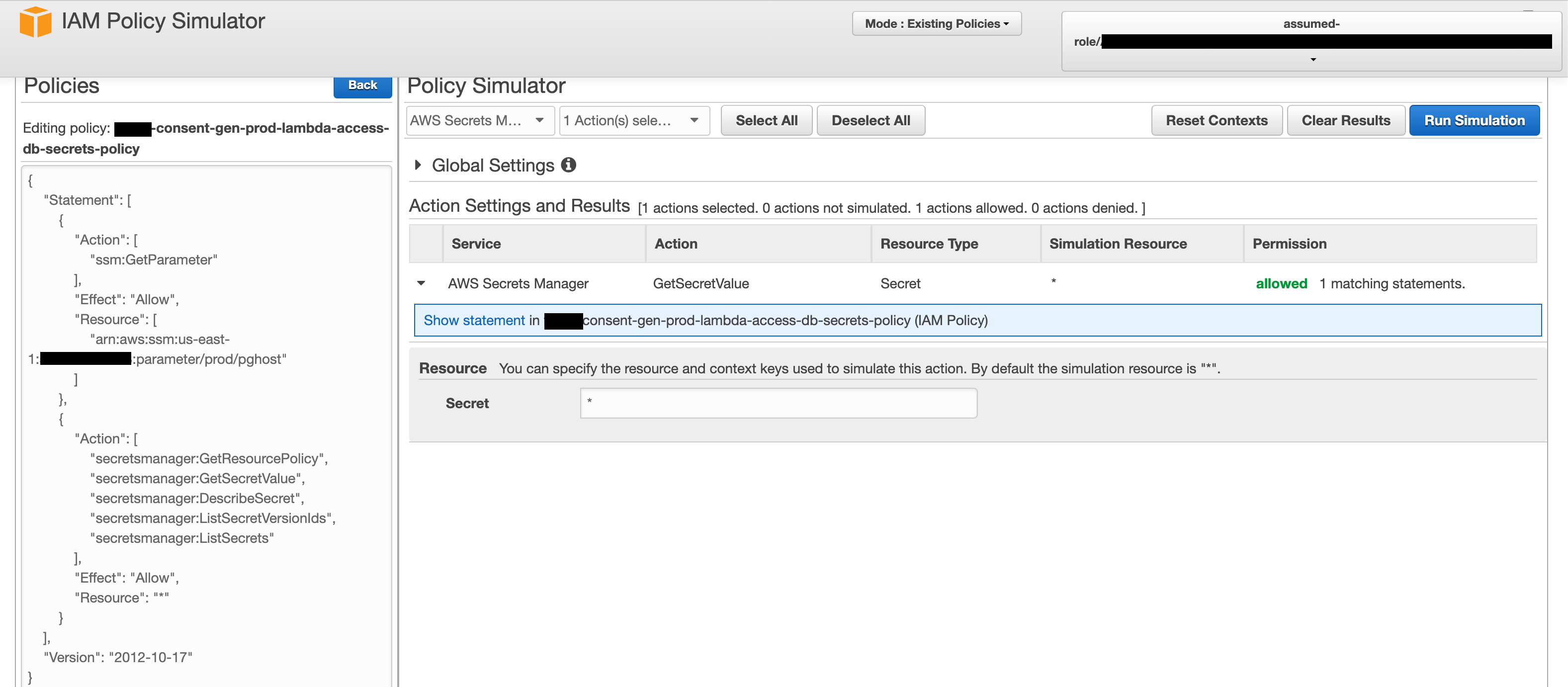
User: arn:aws:sts::#####:assumed-role/consent-gen/consent-gen is not authorized to perform: secretsmanager:GetSecretValue because no identity-based policy allows the secretsmanager:GetSecretValue action
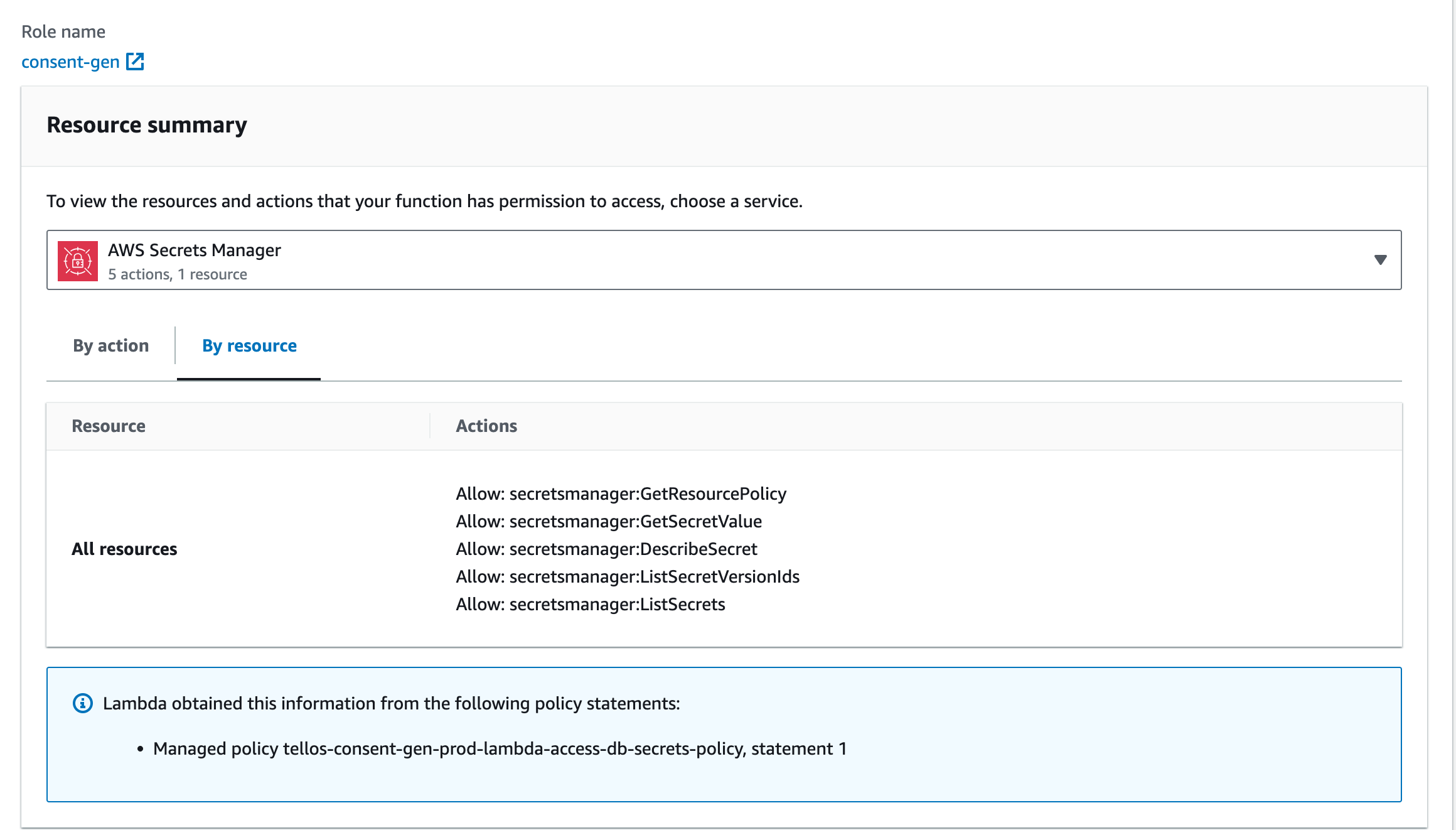
Policy Simulator tells me I have access rights however, in addition to the console telling me I have rights
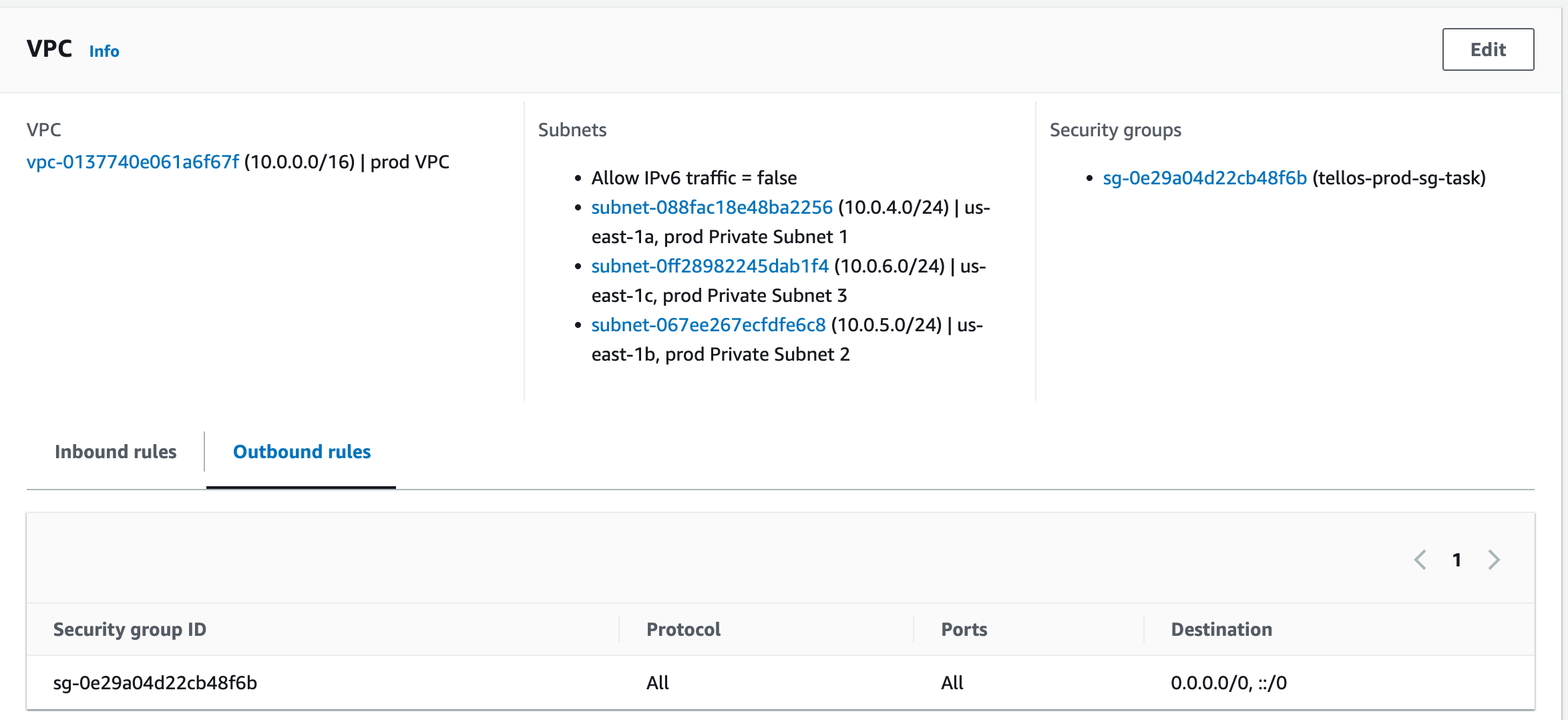
While the lambda is in a VPC, it is in private subnets
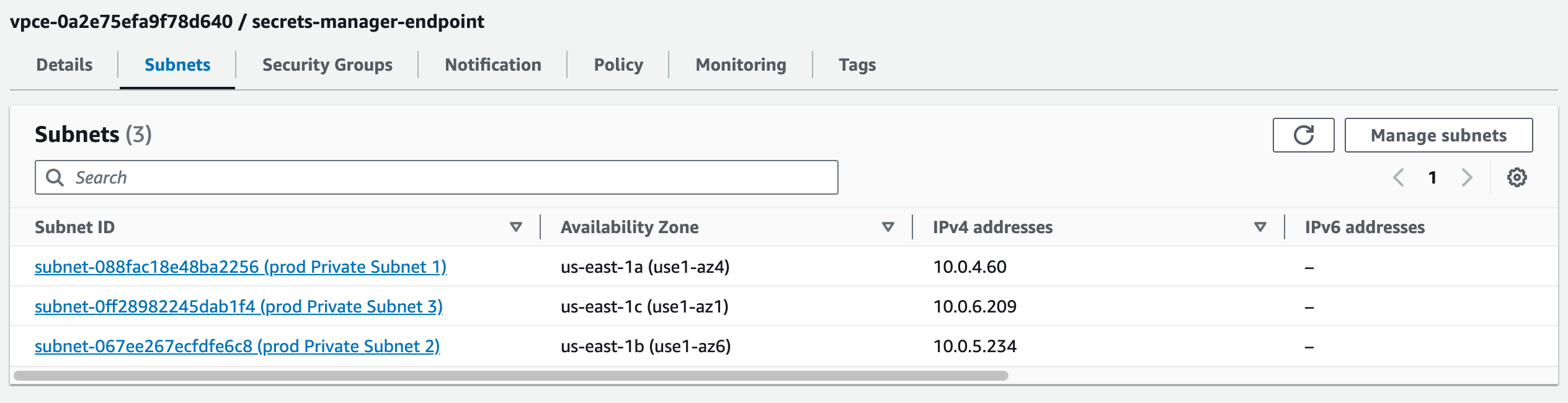
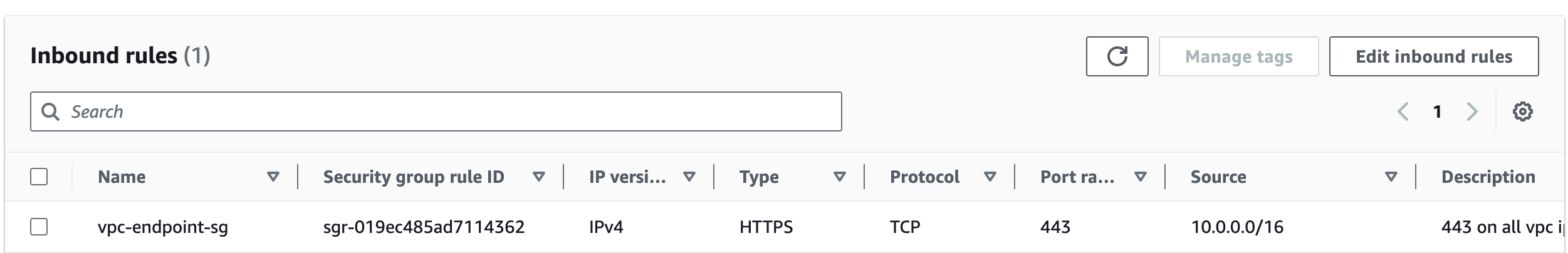
And I have a VPC Endpoint for secrets manager set up, in the same vpc/subnets
with a security group set up to allow inbound traffic from the VPC i’m on
I’m at a loss at this point, has anyone else experienced this?

 Question posted in
Question posted in 

2
Answers
I would check the following:
(Posted solution on behalf of the question author to move it to the answer space).
I did absolutely nothing, but the error disappeared. I’m guessing I needed to wait longer for something in the VPC endpoint to be set up internally to AWS but I honestly don’t know. Such is the mystery of AWS.