I’m building a very basic Dockerfile for a python-based AWS lambda,
Dockerfile (docker build -f Dockerfile -t test-img:0.0.1 .):
FROM public.ecr.aws/lambda/python:3.9
RUN yum update -y && yum install libgomp -y && yum clean all
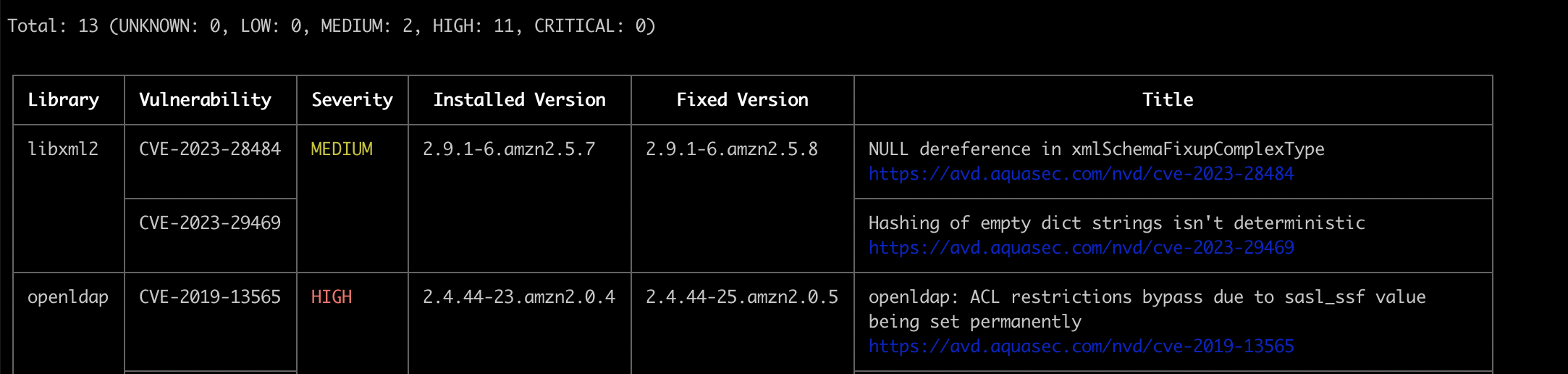
A trivy scan is showing vulnerabilities from openldap. I attempt to yum update openldap and it can’t find the fixed version suggested by the trivy scan, 2.4.44-25.amzn2.0.5, it returns No package openldap-2.4.44-25.amzn2.0.5 available.
trivy --cache-dir .trivycache/ image --ignore-unfixed --no-progress --exit-code 1 --input test-lambda.tar
Does anyone know how I can update to the suggested version?
Security notes here: https://alas.aws.amazon.com/AL2/ALAS-2023-2033.html



2
Answers
I had a similar issue but with a Java-based Amazon image.
I just updated the base image to a version that did not have any vulnerabilities, you may be able to do something similar. I often find that upgrading the base image is the simplest way to go in order to squash image-based dependencies, it at least narrows down the offenders.
For example, I went from
to:
And this fixed Trivy scanner reporting problems with
openldapUntil a new image is published, you can also force the update of the base image within your Dockerfile:
The above cleared the openldap finding in the scans by AWS ECR.