Using ADF, I’ve created a linked service to a Blob Storage on Azure.
The connection to the linked service works:
I added a file to the Blob storage which I can clearly see.
The Blob is defined with the Firewalls and Virtual Networks setting of "Enabled from selected virtual networks and IP addresses".
When I test the connection, it passes the test.
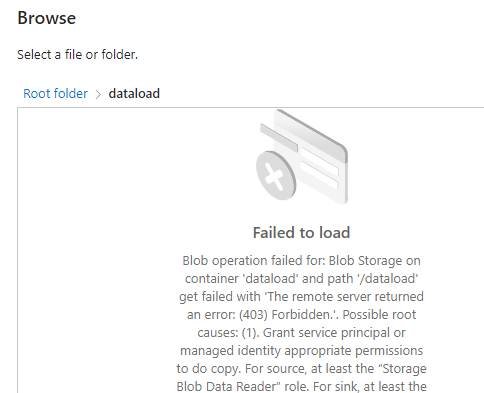
When I try to Browse the folder (it can see the folder!) to the specific file path I get error 403: Forbidden
I’ve tried adding permissions but to no avail.
The ADF has a Read permissions access (I’m talking about the SOURCE file here) to the container.
I’ve also tried adding all the IP addresses of the ADF region (Australia-East).
The Virtual Network is added and all the IP addresses behind which the ADF might sit are also whitelisted for the Blob storage.
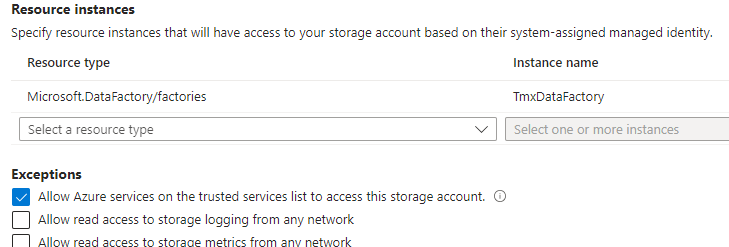
Edit: the Data Factory is whitelisted for the blob storage:
and the access is done based on the System Assigned Managed Identity.
The one thing which I know works, but I don’t want to do, is simply to enable access to this blob storage from ANY network.
Any ideas?





2
Answers
Alright, I managed to solve this issue as follows:
I didn't miss any step, including the approving of the private endpoint to the said blob storage.
That actually let to a different version of the 403 error.
[![enter image description here][1]][1]
And now I can look at the data in the folder: [![enter image description here][2]][2]
And no more error 403 [1]: https://phpout.com/wp-content/uploads/2024/01/roDhI.png [2]: https://phpout.com/wp-content/uploads/2024/01/E47uy.png
To make successful connection follow below steps:
Go to Access control (IAM) in your storage account >> Add >> Add role assignment. For a Role we select
Storage Blob Data Contributorto your data factory managed identity (service principal) which is name of data factory.Allow Azure services on the trusted services list to access this storage accountsetting on storage properties.3. Change authentication method from account key to managed identity.