I’m trying to create an Azure automation system to change the number of always ready instances of a Function App (the App Service Plan is Elastic Premium One EP1):
The Automation System is created in order to set the number of Always Ready Instances to 3 during week days, and set it to 1 during weekend days.
The System is composed by the following two runbooks created under the service Azure Automation Accounts:
- "runbook-Weekdays"
$resourceGroupName = "xxxxxxxxxxxx"
$functionApp = "xxxxxxxxxx-func"
$Resource = Get-AzResource -ResourceGroupName $resourceGroupName -ResourceName $functionApp/config/web -ResourceType Microsoft.Web/sites
$Resource.Properties.minimumElasticInstanceCount = 3
$Resource | Set-AzResource -Force- "runbook-Weekend-days"
$resourceGroupName = "xxxxxxxxxxxx"
$functionApp = "xxxxxxxxxxxx-func"
$Resource = Get-AzResource -ResourceGroupName $resourceGroupName -ResourceName $functionApp/config/web -ResourceType Microsoft.Web/sites
$Resource.Properties.minimumElasticInstanceCount = 1
$Resource | Set-AzResource -ForceNote that I’m using a "System Assigned" identity in my Automation Account.
While the automation logic is implemented using Azure Logic Apps:
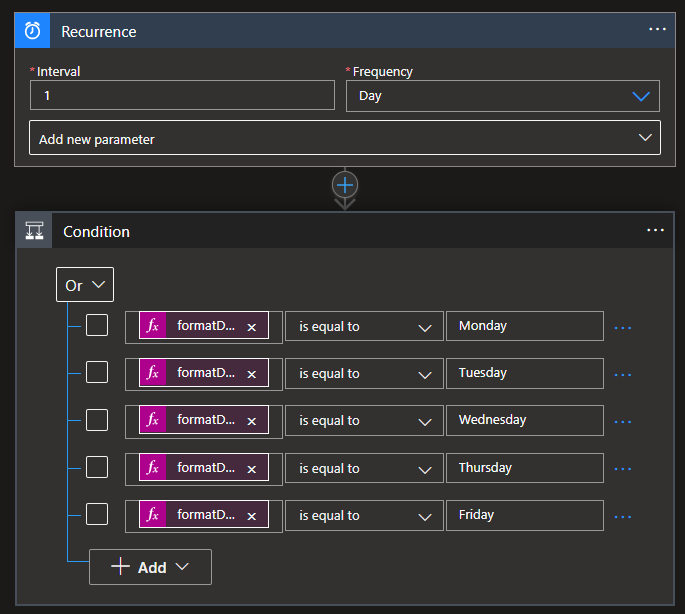
Where the expression under the "Condition" box is: formatDateTime(utcNow(),'dddd'), which set only for the week days as can be seen from the previous figure.
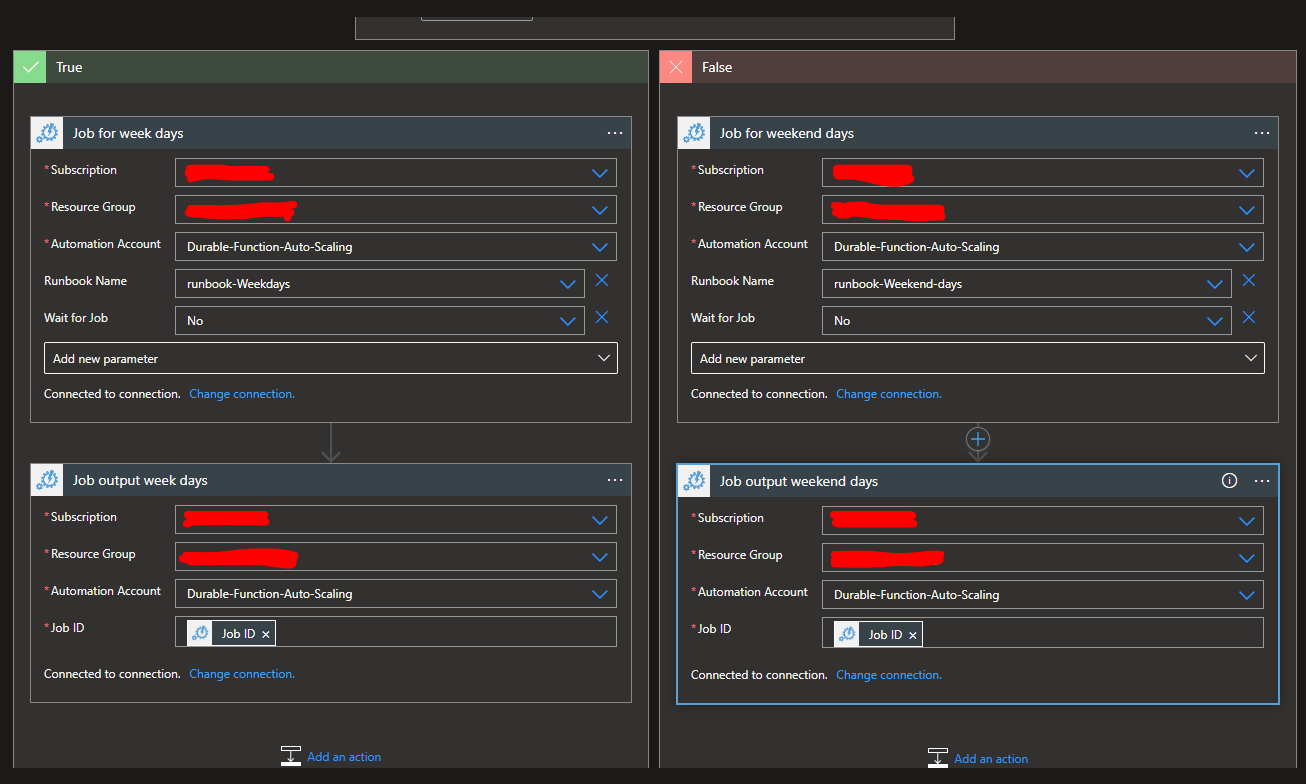
The following figure is the second part of the Logic App:
Note that, when creating the Automation Job in Logic Apps, I have selected "OAuth default" as authentication method, then I simply pasted the tenantID of my subscription.
Now, if I test the Logic App from the Logic App service, it works:
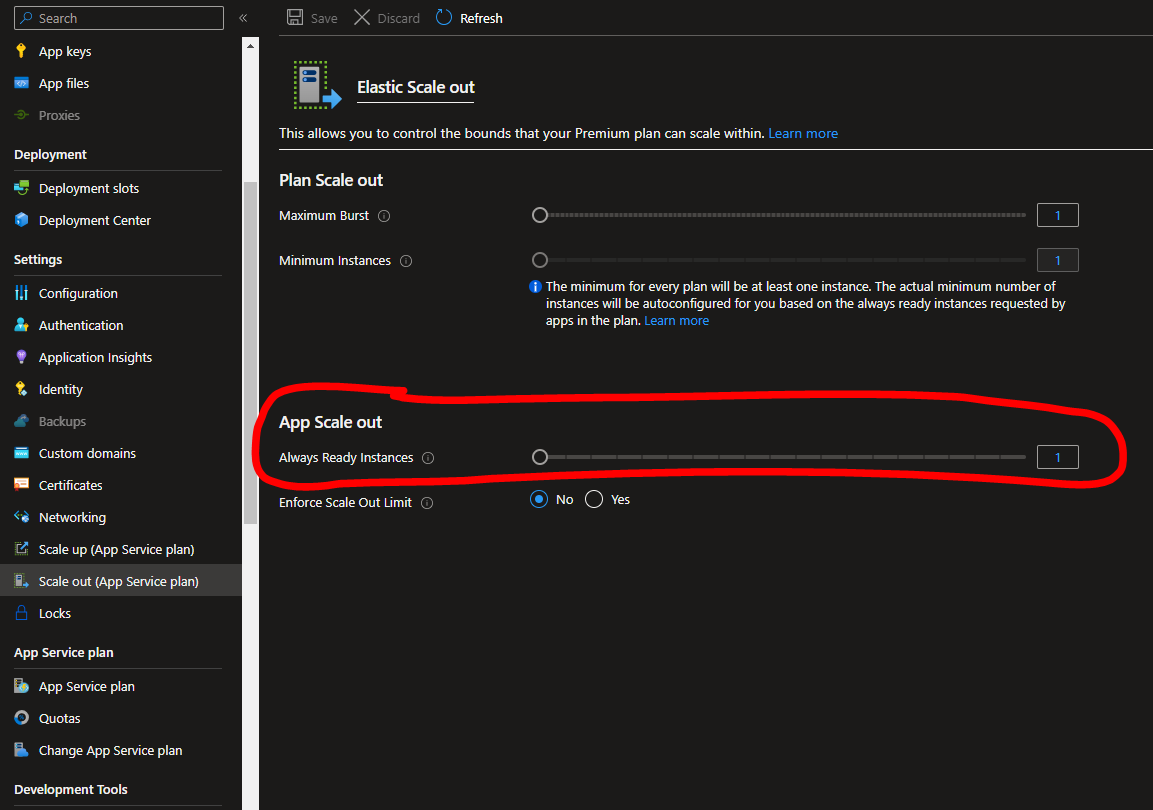
And I would expect a number of always ready instances equal to 3, but if I check the number of always ready instances, nothing changed:
Also, going to the errors page of the runbook page:
I see the following two errors:
Get-AzResource : Run Connect-AzAccount to login. At line:4 char:13 + $Resource = Get-AzResource -ResourceGroupName $resourceGroupName -Res ... + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : CloseError: (:) [Get-AzResource], PSInvalidOperationException + FullyQualifiedErrorId : Microsoft.Azure.Commands.ResourceManager.Cmdlets.Implementation.GetAzureResourceCmdletand
The property 'minimumElasticInstanceCount' cannot be found on this object. Verify that the property exists and can be set. At line:5 char:1 + $Resource.Properties.minimumElasticInstanceCount = 3 + ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : InvalidOperation: (:) [], RuntimeException + FullyQualifiedErrorId : PropertyNotFoundDo you know what could be the problem?






2
Answers
The error "Run Connect-AzAccount to login" indicates that the call to run the command is not made in a security context that is allowed to make the call.
In your case it is the logic app that is making the call. So first thing to check is the security context of your logic app.
Have you logged in within your runbook?
The first error tells you to connect using
Connect-AzAccountand the 2nd error is a generic error that the property doesn’t exist because$Resourceobject doesn’t have that property.If you’re still using the runas account with a certificate it would look like:
If you’re using a system assigned identity then you will need to include the relevant authentication code for that instead
https://learn.microsoft.com/en-us/azure/automation/enable-managed-identity-for-automation#authenticate-access-with-system-assigned-managed-identity