I have been using my personal MS account (actually a gmail account I use to log into my personal MS account and azure portal). I have a bunch of applications in azure and DNS services, etc all using this account. Well for one of my ASP.NET Core Web APIs I am using managed identities for the app service to interact with the app registration which has been granted application permissions for users.read.all, calendars.readwrite , files.readwrite, mail.readwrite, and contacts.readwrite. However, I am only able to make requests to the users.read.all scope and basically pull a list of users. I return an error when trying the others and from searching for an answer I have been reading that personal MS accounts are unable to use MS Graph API with service accounts and application permissions. It is unclear if this is true or not as I do have a button in my Azure Portal that says grant admin consent and I do see those permissions in my enterprise application on the gui. I am asking this question primarily because I find some of the info online unclear as it says you can assign application permissions in the personal account but you cannot grant admin permission in the personal account hence the reason you need a business account. My azure portal in the app registrations in API permissions show a grant admin consent button so its unclear if that is just dated information.
So related to the general question I was hoping to get clarity on the following items. This is also tied to a post I did earlier trying to debug the issue:
Using Azure MS Graph API Service Account with Managed Identity
- Is upgrading to a business account required for this type of scenario?
- If go to choose one of these MS packages in the business section will these permissions magically be approved and I can go on my way with my MS Graph api requests?
- In azure portal logged in via my personal account when I created a new user for my active directory, was that account inherently personal as well since my primary is?




2
Answers
Application Permissions (aka the Client Credential OAUTH flow) require Admin Consent. Since consent cannot be granted for consumer/personal resources, the Client Credentials flow is not supported for a Microsoft Account (MSA).
From the document All delegated permissions are valid for work or school accounts, but not all are valid for personal Microsoft accounts. Use the Microsoft Graph permissions reference to identify delegated permissions that are valid for personal Microsoft accounts, Please refer this for the document for permissions reference:https://learn.microsoft.com/en-us/graph/permissions-reference
For licensing when using Microsoft Graph API: https://azure.microsoft.com/en-us/pricing/details/active-directory/
Hope this helps.
I created an Azure Web App and turned-on System Identity like below:
In the Enterprise Application, I assigned below permissions:
Generated access token via Kudu:
By using the above access token, I am able to call the message endpoint like below:
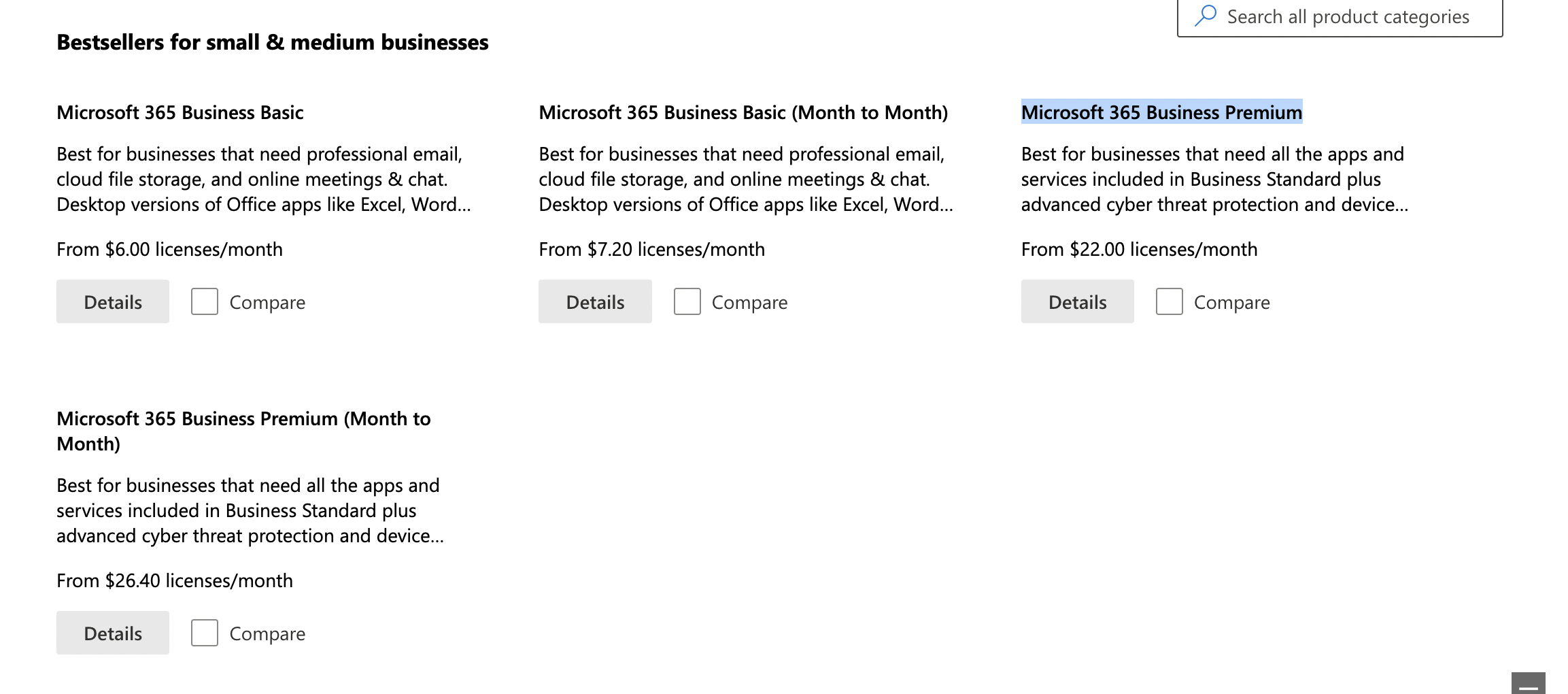
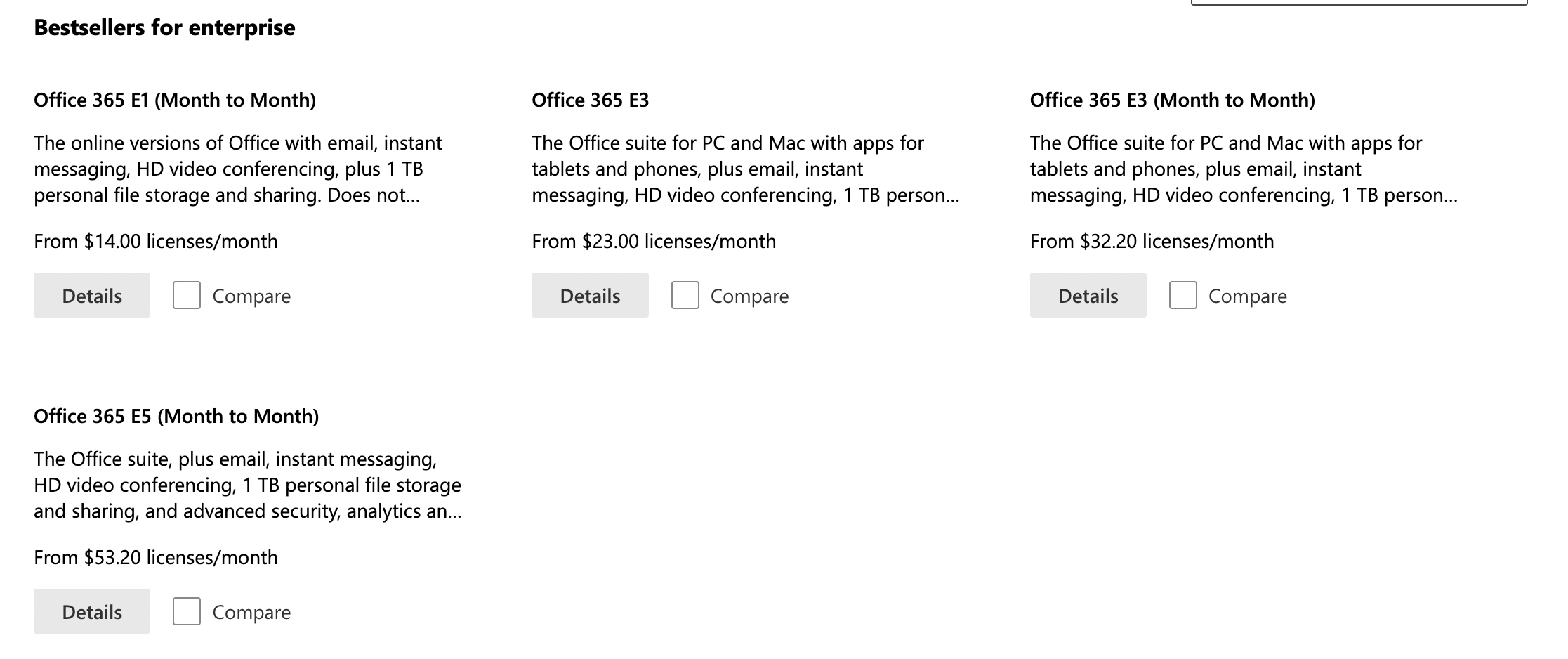
In your case, to resolve the issue try upgrade to the Business package and assign the user with the license:
Assign the Business package based on your requirement like below:
Note that: I agree with @Mehtab Siddique, Admin consent is not supported for personal resources and not all delegated permissions support personal accounts.