I am following this article to create a simple app service wiht container image pulled from an ACR: https://learn.microsoft.com/en-us/azure/app-service/tutorial-custom-container?tabs=azure-cli&pivots=container-linux.
Everything works fine, except the last webhook part where the app service will be notified in case there is an updated image available. The web hook call from ACR to app service always returning 401 unauthorized. Same behavior from fiddler call in case I try to access the web hook endpoint directly using a POST ping command. It seems the basic auth to access the SCM of the web app is not working.
Steps:
- Create an acr and pull a default image from MCR into the ACR to use later in the web app and enable admin access/keys for the ACR.
2: Create a linux based container web app pointing to above ACR using admin key & use the image pulled earlier.
At this point the web app is up in a few seconds after the initial pull.
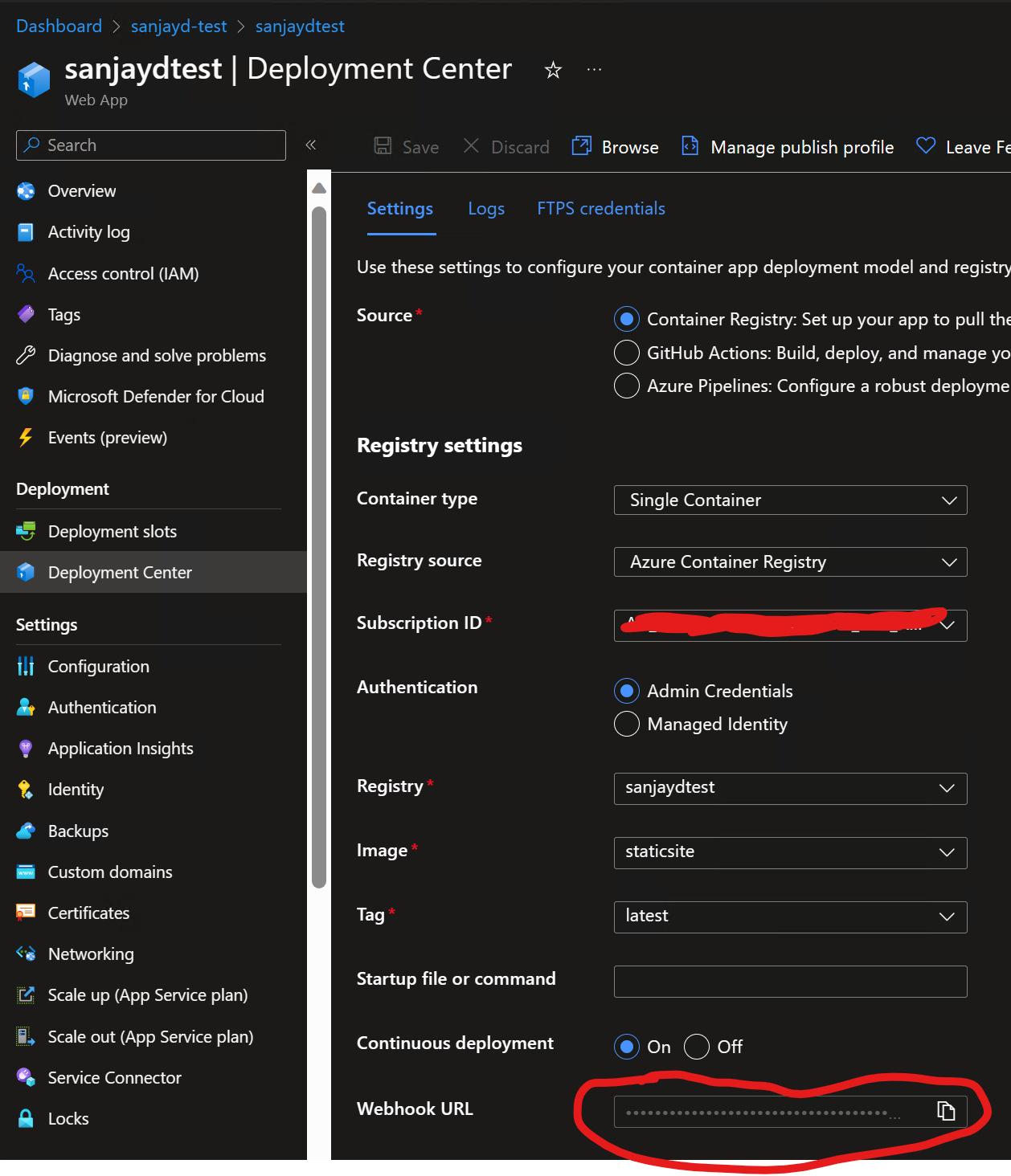
- Now enable continuous integration in the web app, that will create a webhook in the ACR automatically.
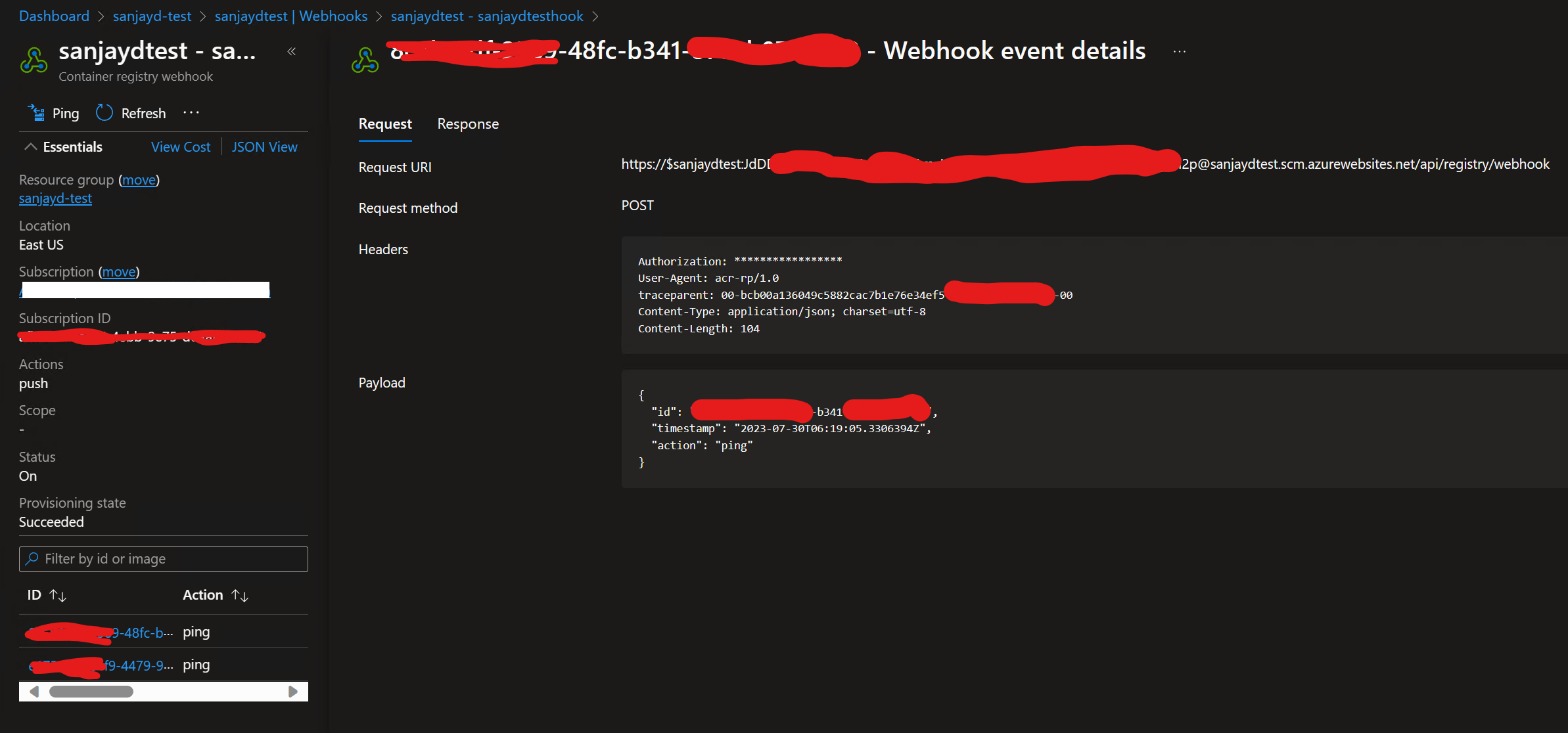
- Go back to the webhook of the ACR & try ping test, which fails with 401 unauthorized.
- Additionally take the web app’s WebHook URL & try accessing the same using a CURL/postman/fiddler POST call, same failure with 401 unauthorized.
- Try pushing the same image to ACR with –force flag to rigger the webhook, then check logs & see the same 401 error in the webhook
What am I missing here?




2
Answers
In this step make sure you are copying the password of ACR correctly.
And make sure you have sufficient role assigned, to create and assign the role with the command below:-
Its necessary to add
AcrPullrole to a "Managed Identity or Service Principal".In addition to this, You can attempt to regenerate the admin keys and access for the ACR and then build the webhook with the new keys. Additionally, confirm that the webhook URL produced by the
az webapp deployment container configcommand is accurate and that the registry name and resource group you provide when creating the webhook are both valid.You can refer this steps and enable container logging.
Try to pass custom authorization Header in ACR webhook Configure settings by referring to the paylod here
Check the Azure Web app logs and validate if the Web app is running successfully, If Web app runs successfully the Webhook ping will be successful.
Refer this answer by Jahnavi for more details.
Ran into this issue myself recently. It turned out that we had disabled the "Basic Auth Publishing Credentials" setting for the App Service. Since the webhook uses basic auth for authentication, this needs to be enabled for it to work. Once we enabled this setting, the webhook started to work as expected.
App Service Settings Screenshot