I need the managed identity client id for setting up auth between an Azure Function and a service bus. I’ve solved it with a user-assigned identity, but would like to achieve it with a system-assigned identity.
I’ve removed some irrelevant from the screenshot below, but see the autocomplete, I can’t see any clientId/applicationId.
When using a user-assigned identity, it’s solved as here.

 Question posted in
Question posted in 

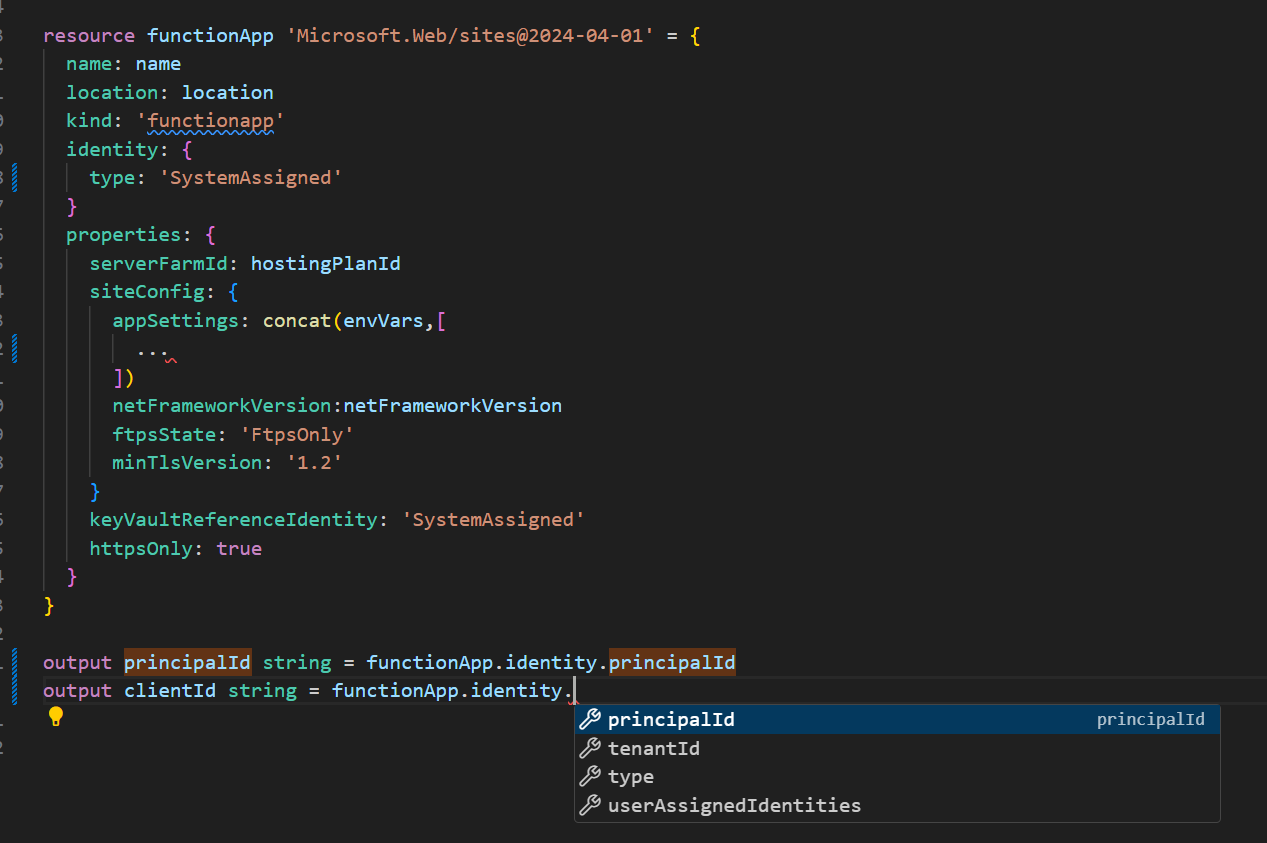
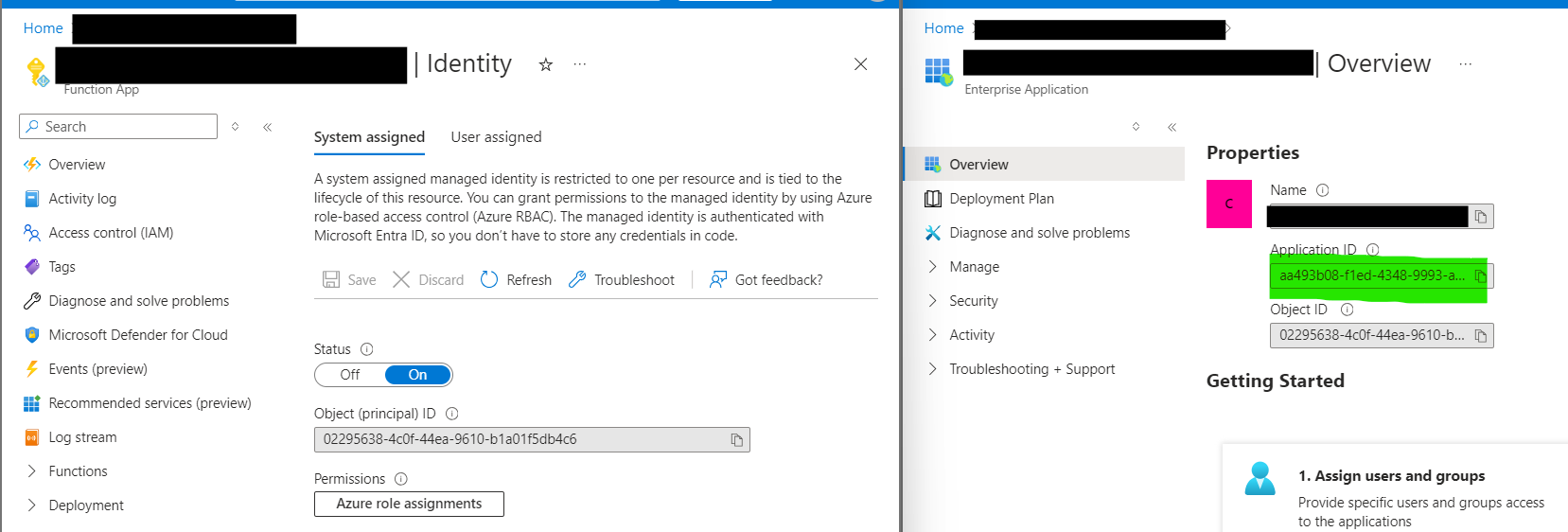
2
Answers
@Julian Hüppauff put me on the right track, I don't actually need it.
I was messing with a template that had previously been setup for a user-assigned identity, I can't seem to find an official reference for it, but apparently you need to set these 3 for a function app when using user-assigned identity and want to connect to a service bus namespace.
When using system-assigned identity, I can simply remove these 3, so no need to lookup the
clientIdin the bicep.An ugly solution, but it works. To simplify, I used logicapp to replace your site, there is no difference in essence.
Create a
user-assigned managed identity, which be used to give access to deployment script.Assign a
Global Readerrole to theuser-assigned managed identityuse
Get-AzADServicePrincipal -ObjectId $objectIdgetapplicationIdFromobjectId, then output it.DeploymentScript
I have also tried Microsoft.Graph servicePrincipals, but be in vain, because, the
service principal bicep - existingalso need applicationId as parameters to fill-in