I have automated the process of creating custom rules on Azure Application Gateway WAF. However, whenever I update any existing custom rule, it automatically removes all other custom rules. I have been unable to find a specific command in the Azure PowerShell documentation to update individual custom rules. I have also raised this issue with Microsoft, and they have confirmed that the command is not available in Azure PowerShell.
During my research, I discovered that we can achieve this by using the ".Add" and ".Remove" operations. However, I am encountering some errors while attempting to do so.
Currently, I am trying two approaches:
-
Adding new malicious IPs to the specific existing custom rule. When I try to execute this, I receive the following error message:
PS C:Usersjaputhiyakath> $policy = Get-AzApplicationGatewayFirewallPolicy -Name $policyName -ResourceGroupName $policyRG PS C:Usersjaputhiyakath> (($policy.CustomRules | Where-Object {$_.Name -match "IPRestrict"}).MatchConditions.MatchValues).Add('2.3.6.9') MethodInvocationException: Exception calling "Add" with "1" argument(s): "Collection was of a fixed size." -
Remove the IPRestrict custom rule from the firewall policy and replace it with a modified custom rule. The approach of working well using
.RemoveAt(0), but we might encounter difficulties in determining the exact position of the object to be removed.I attempted to remove the object using the command provided below, but despite the absence of any errors, the object remains unaffected and does not get removed.
PS C:Usersjaputhiyakath> ($policy.CustomRules | Where-Object {$_.Name -match "IPRestrict"}).Remove
For Reference;




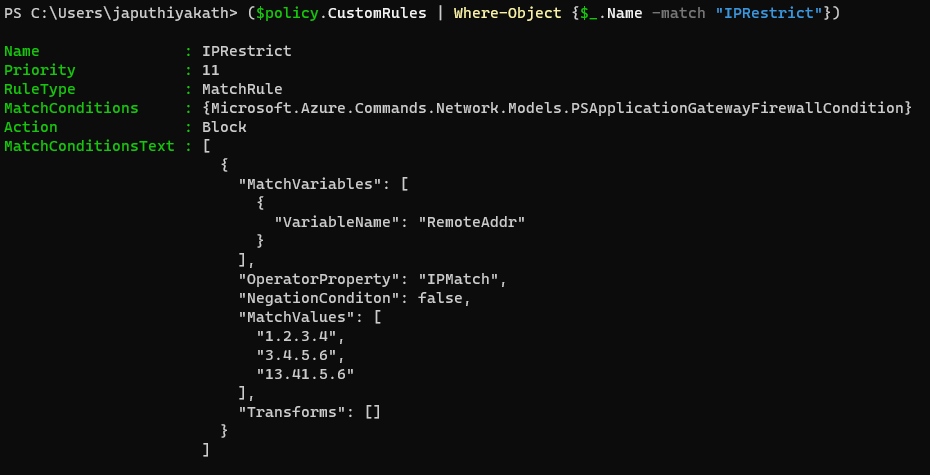
2
Answers
I think a more PowerShelly way is to;
As an aside:
Where-Object Name -eq IPRestrictrather thanWhere-Object {$_.Name -match "IPRestrict"}is used below to identify the policy of interest:-eqensures literal, full-value matching, whereas-matchalso finds substrings (by way of a regex pattern). Separately, the omission of{ ... }and$_is an application of simplified syntax.Re 1:
It isn’t obvious, but your command applies member-access enumeration, because the
.MatchConditionsand also the.MatchValuesproperty contain lists (array-like collections of typeSystem.Collections.Generic.List`1).Due to the resulting member-access enumeration,
.MatchConditions.MatchValuesreturns a regular .NET array (System.Arraycontaining the.MatchValueslist entries across all.MatchConditionlist entries..Add()method in the context of implementing theIListinterface.To successfully extend the list stored in
.MatchValues(which does support.Add()), you either need to identify which particular.MatchConditionslist entry you want to target or you must iterate over all.MatchConditionslist entries and call.Add()on each (assuming that makes sense); e.g.:Re 2:
The
System.Collections.Generic.List`1type has a.Remove()method that allows you to pass the object to remove from the list rather than having to know its index in the list: