We are running Python scripts in Azure Data Factory using Batch Service of Azure Data Factory.
We are reading secrets from key vault using Service Principle for which we need to hardcode the Client Id, Client Secret which has the access to read secret values.
Is there any way to overcome this problem so that there is no requirement of hardcoding the Service Principle.
Can we use Managed Identities in this case?
We tried using Managed Identities and we created a User Managed identity to access the key vault.
The Batch Account and Azure Data Factory has been provided the access to this User Managed Identity.
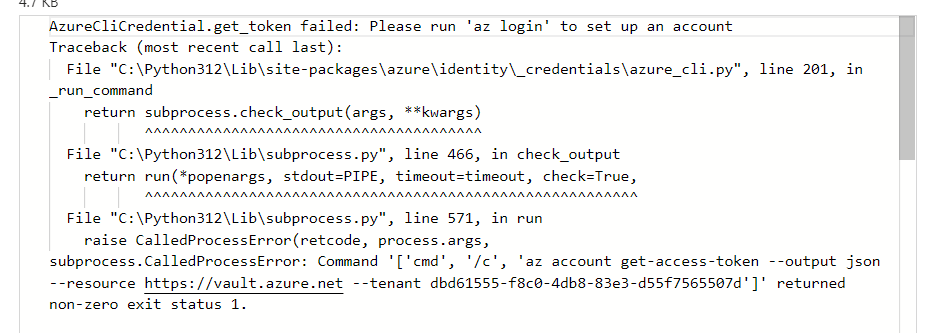
But we are unable to find the next steps in the same case.
We have User-Assigned managed identity which has been associated to both Data Factory and Batch Account and this Managed Identity has Secret read permissions as well.
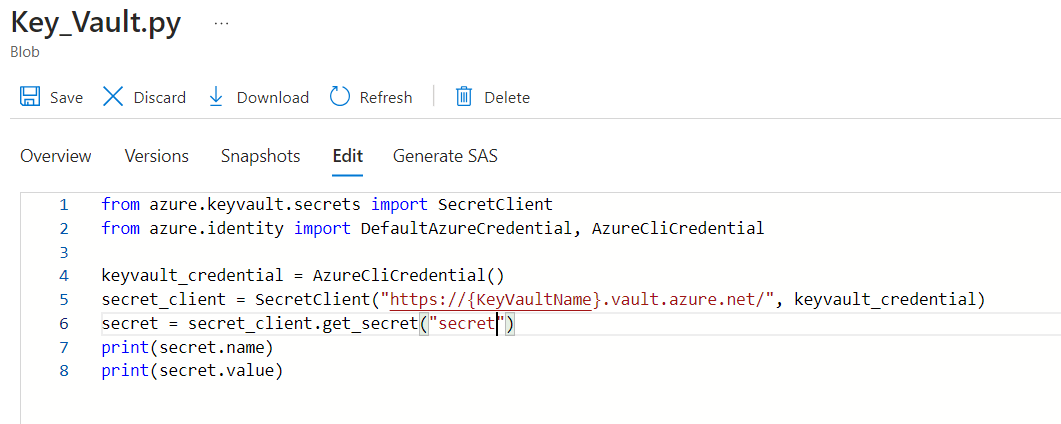
Running the below python script to read the Secrets.
But the issue now we are facing is defined below:
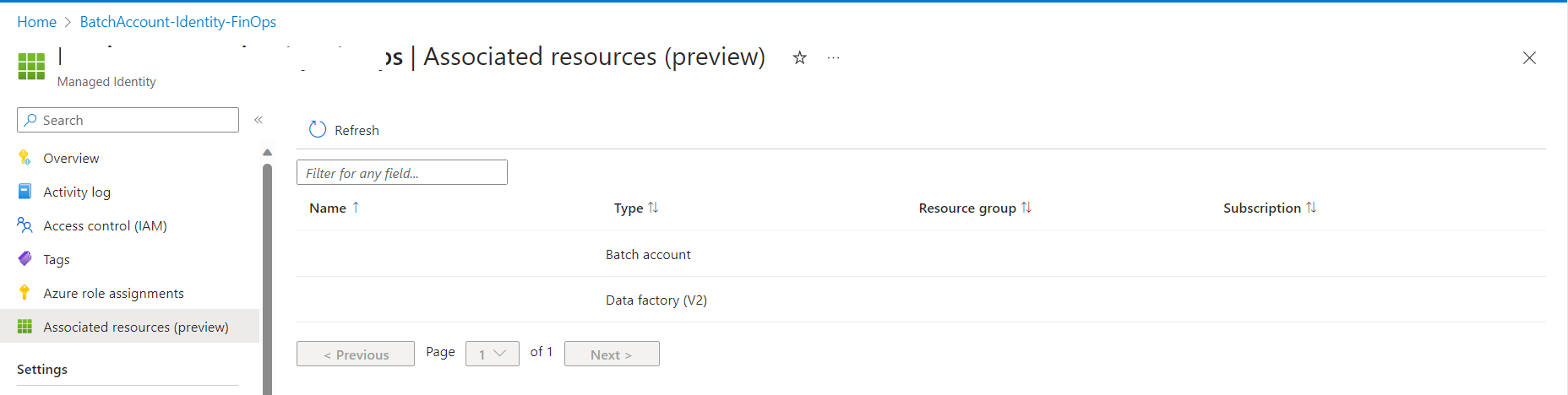
The managed identity has the following associated resources :

 Question posted in
Question posted in 

2
Answers
When we are developing Azure Batch Account and deploying pools in the Batch Account the created Managed Identity should have Secrets Read permissions.
The Managed Identity should be associated to the below mentioned resources in this case .
We were not associating Managed Identity to the pool created and was facing this error. The below Python Script worked for me.
Thanks
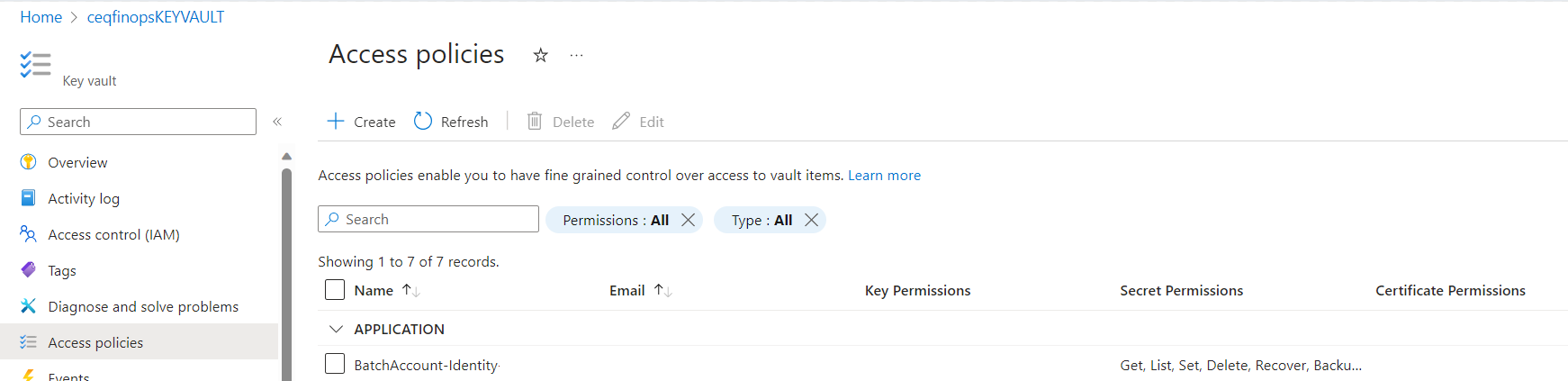
Managed identity doesn’t have permission to get the secret; that may be the reason for the error above. Give the required permission to the managed identity in Key Vault by following the procedure below:
Create an access policy in Key Vault as follows:
Go to access policies in Key Vault, click on
Create, select the permissions and the identity, and then click onReview+create, as shown below:After creating the access policy, you will be able to get the secret from Key Vault successfully using the code below: