I have an Azure policy with a "Modify" effect:
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Web/sites"
},
{
"field": "Microsoft.Web/sites/publicNetworkAccess",
"exists": "false"
}
]
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/b24988ac-6180-42a0-ab88-20f7382dd24c"
],
"operations": [
{
"condition": "[greaterOrEquals(requestContext().apiVersion, '2022-09-01')]",
"operation": "addOrReplace",
"field": "Microsoft.Web/sites/publicNetworkAccess",
"value": "Disabled"
}
]
}
}
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"Modify",
"Disabled"
],
"defaultValue": "Modify"
}
}
}
As I understand, this policy will set the attribute "publicNetworkAccess" of resource "Microsoft.Web/sites" to false if the attribute does not exist
After assigning the policy to my only subscription, I used ARM template to deploy the "Microsoft.Web/sites" resources:
{
"type": "Microsoft.Web/sites",
"apiVersion": "2021-02-01",
"name": "[parameters('webAppName')]",
"location": "[parameters('location')]",
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]"
],
"identity": {
"type": "SystemAssigned"
},
"properties": {
"httpsOnly": true,
"serverFarmId": "[resourceId('Microsoft.Web/serverfarms', variables('appServicePlanPortalName'))]",
"siteConfig": {
"linuxFxVersion": "[parameters('linuxFxVersion')]",
"minTlsVersion": "1.2",
"ftpsState": "FtpsOnly"
}
}
}
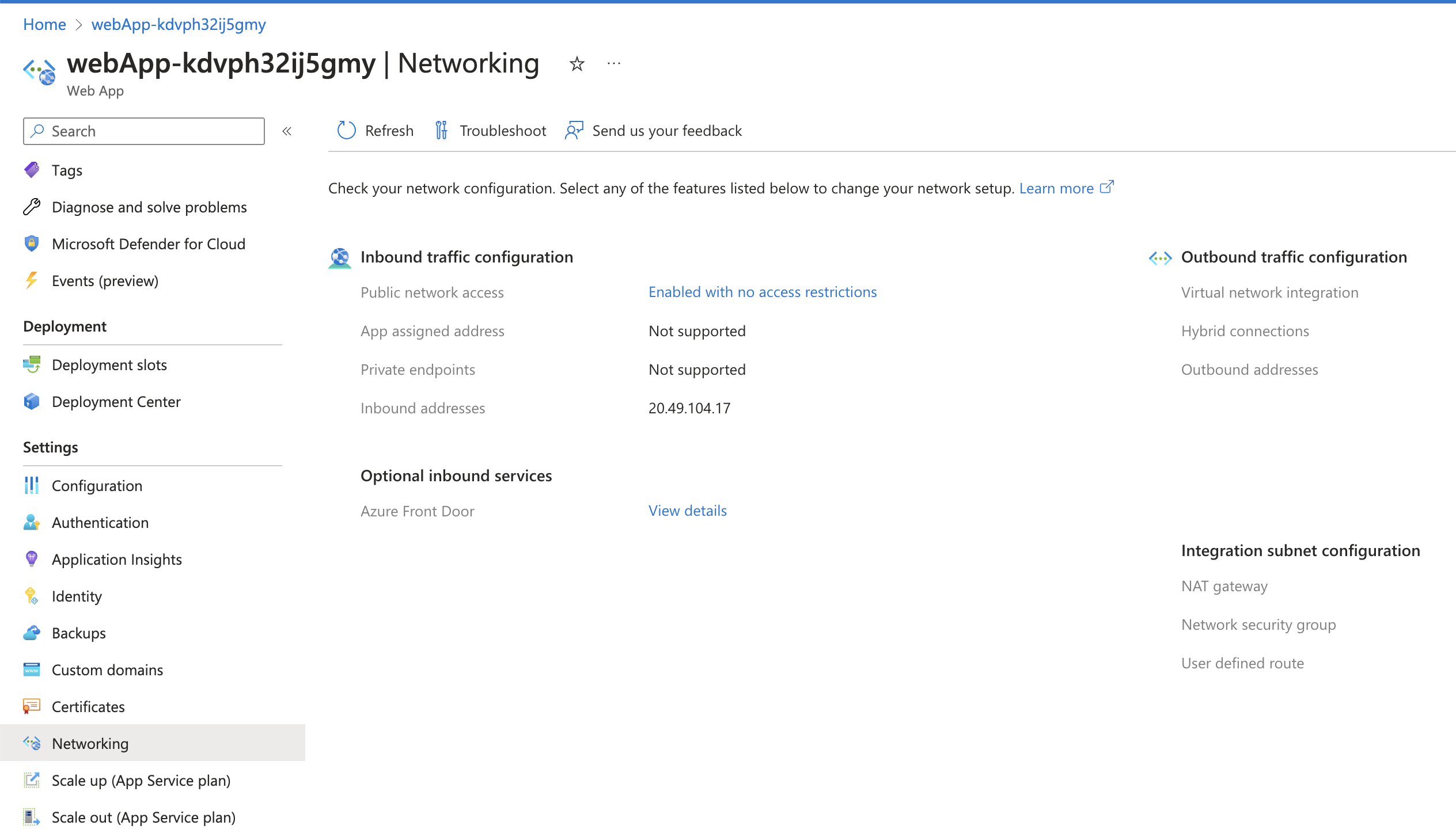
However, after the deployment is completed, I check the app service and see that the "publicNetworkAccess" is set to "Enabled":
It means that the policy does not take effect. What’s wrong with my policy ?

 Question posted in
Question posted in 

2
Answers
Change your
policyRuleto includeanyOflike this (this is best practice):For sake of learning, then use PS this to check if the property is modifiable:
Remember that the
policyRuleonly proceed if the condition is evaluated as ‘true’.By default, the
web appwill have this value"publicNetworkAccess": null, which means that the aboveif-statement is true.Reason for non-compliance: Current value must exist.Now the policy is ready for remediation.
You are using
Contributoras permissions for the (system assigned)managed identity, this is overprivileged, but will of course worked.To follow the process, you can run this to get all the properties of your web app BEFORE the
remediation:$webappit is empty. You can also confirm by running this:Now run your policy remediation, once completed, repeat the
$webapp = Get-AzResource-command steps to refresh the variable.Here is the updated
Azure Policyto disable thepublicNetworkAccessproperty forAzure Web Apps(Microsoft.Web/sites) only if it is alreadyenabled.While assigning the policy, make sure to enable the
remediation taskto implement changes as follows.The policy has been updated to disable public access for web apps.
The public access for the web app has been set to disabled.