Within Azure Sentinel, I have several automation rules set up that respond with various playbooks/logic apps.
I want to be notified or know how to search the logs to find all the
- failed runs
- failed actions (by playbooks/logicapps) and
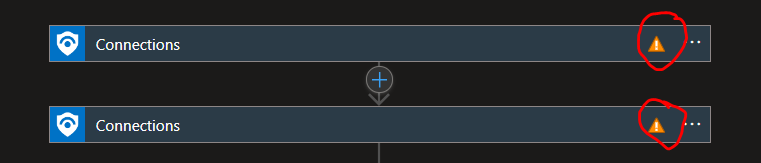
- when a playbook connection is disconnected (see screenshot below).
The closest I’ve gotten to this is via azurediagnostics logs but Im noticing this only captures less than 1% of the logic apps in my environment.
AzureDiagnostics
| where OperationName contains "Microsoft.Logic"
| extend OperationType = tostring(split(OperationName,'/')[2])
| extend LogicApp = tostring(split(ResourceId,'/')[8])
| extend IncidentNumber = toint(extract(@"[a-f0-9]{8}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{12}_(d+)", 1, correlation_clientTrackingId_s))
| summarize Resource = strcat_array(make_set(Resource),', '),
status_s = strcat_array(make_set(status_s),', ') by LogicApp, IncidentNumber, OperationType, Level




2
Answers
This KQL will show All Logic App Failures, however, will not show when a connection fails.
You can create an alert rule on a logic app:
