I think I am having a misconfiguration and going through the docs in the pas few days still having the following issue.
- I have a web app which uploads to a blob in azure and it works fine.
- my requirement is only people who are in the azure ad will be authorize to open the files from the link
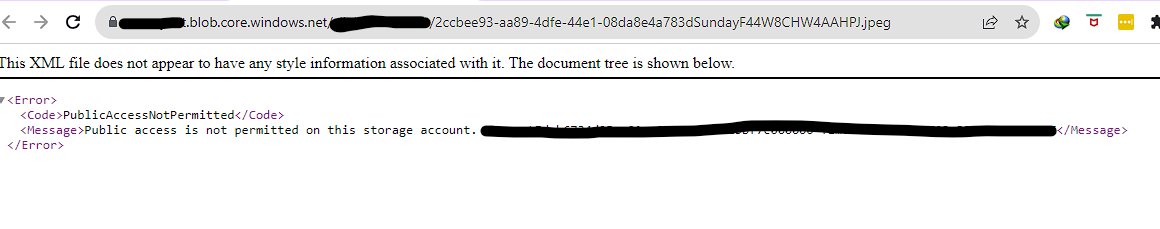
what I do is after uploading the file it has a hyperlink on the UI which works fine if the anonymous access to the storage is enabled.
But what I want is only people who are in the current active directory will be able to see the link.
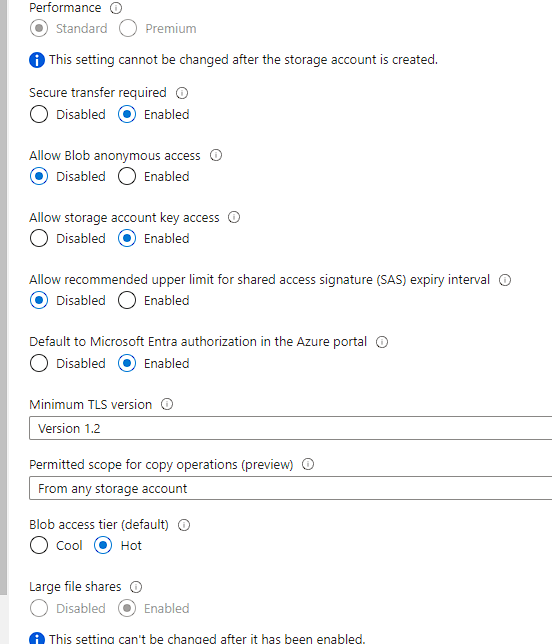
So I am logged in and have the current configuration on the Azure storage config
and then when I click on the link I get
and when it comes to IAM, I added Storage Blob Data Contributor role to my user.
I was wondering what would I be missing?




2
Answers
Thanks for the response, @venkatesan reply is similiar to my final solution where instead I made a function in the app where when the user clicks on the link app generates a token that adds to the hyperlink and the link is only valid for 1 second in our case.
I agree with Thomas’s comment, In the browser, the request doesn’t include any OAuth token.
In my environment, I had configured as same as you:
Portal:
If you need to authorize the user to authenticate with Azure AD first you need to fetch the oauth token from the user.
You can use the below Python code that will authenticate with Azure ad and authorize you to open the files from the link.
Code:
First in your terminal login
az-loginand In the above code are using theAzure Identitylibrary to authenticate and get a token for accessing Azure Storage.Token making as
GETrequest to read the contents of a filereadme.txtstored in an Azure Blob Storage containervenkat678.blob.core.windows.net/test.Output:
Reference:
azure.identity.DefaultAzureCredential class | Microsoft Learn