I’m developing an Outlook add-on that requires Mail.ReadWrite permission.
I have added this permission in my registration app in Azure in my tenant ( Tenant A ).
I have also added them in the manifest.xml file
<Scopes>
<Scope>Mail.ReadWrite</Scope>
<Scope>offline_access</Scope>
<Scope>User.Read</Scope>
<Scope>profile</Scope>
<Scope>openid</Scope>
</Scopes>
Here’s how I call the login prompt (using Office.js library )
const token = await OfficeRuntime.auth.getAccessToken({
allowConsentPrompt: true,
allowSignInPrompt: true,
forMSGraphAccess: true,
});
Then I’m testing with a second tenant.
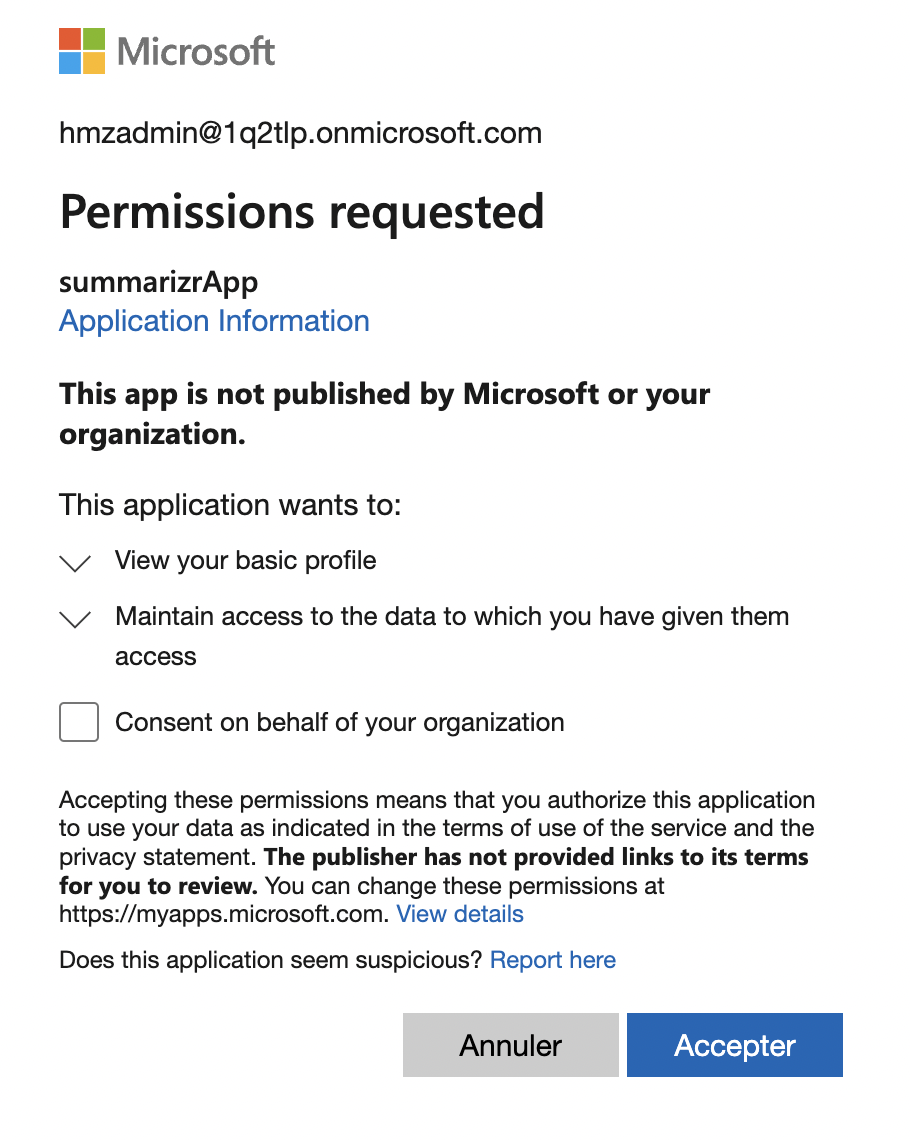
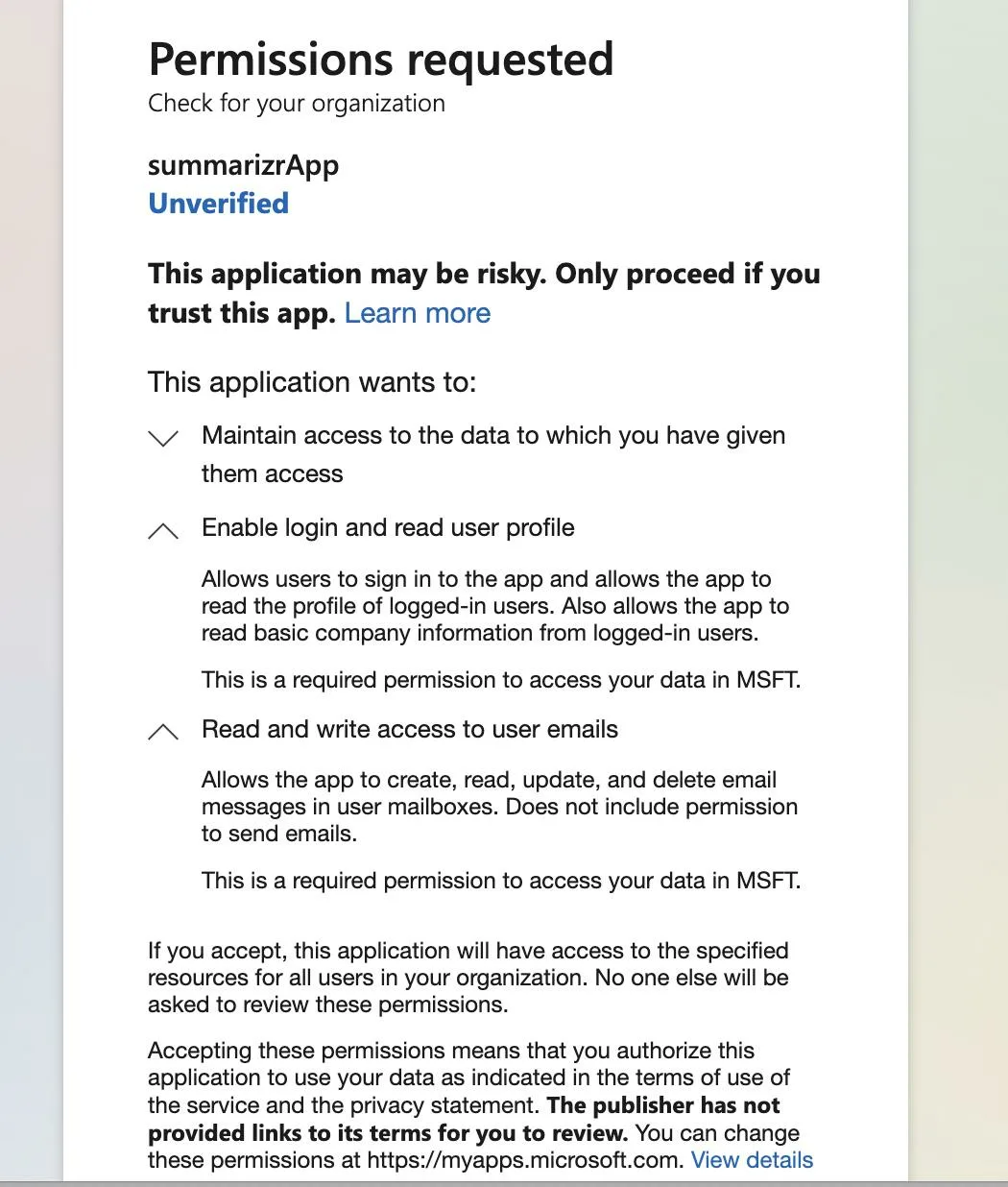
When the user in tanant B installs the add-in and run the app for the first time. A pop-up consent appears
Here I don’t see all the permissions that the app requests.
That causes an issue when I try to get graph API data. I get this error:
‘AADSTS65001: The user or administrator has not consented to use the
application with ID ‘1bc20309-c580-40ad-8133-c0c2bd127807’ named
‘summarizrApp’. Send an interactive authorization request for this
user and resource.rnTrace ID:
bb0919d6-3fbe-4a62-b5a3-7389b3da4100rnCorrelation ID:
76194227-9c13-4292-9088-aac8a7d037f1rnTimestamp: 2023-06-09
16:34:38Z’
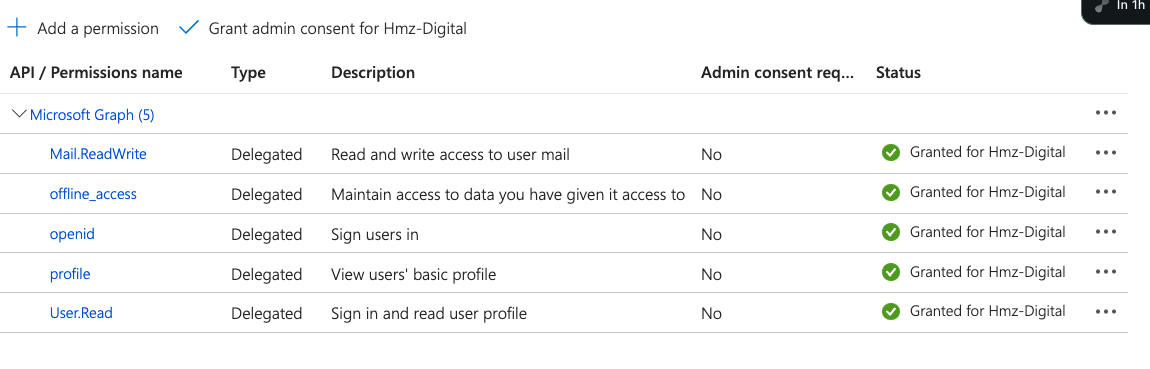
When I log into Entreprise applications on test tenant B Azure portal I see that the app is added.
But I notice that not all permissions are there, only profile, openid, and offline_access but not Mail.ReadWrite or User.Read
Yet These permissions don’t need an admin grant.
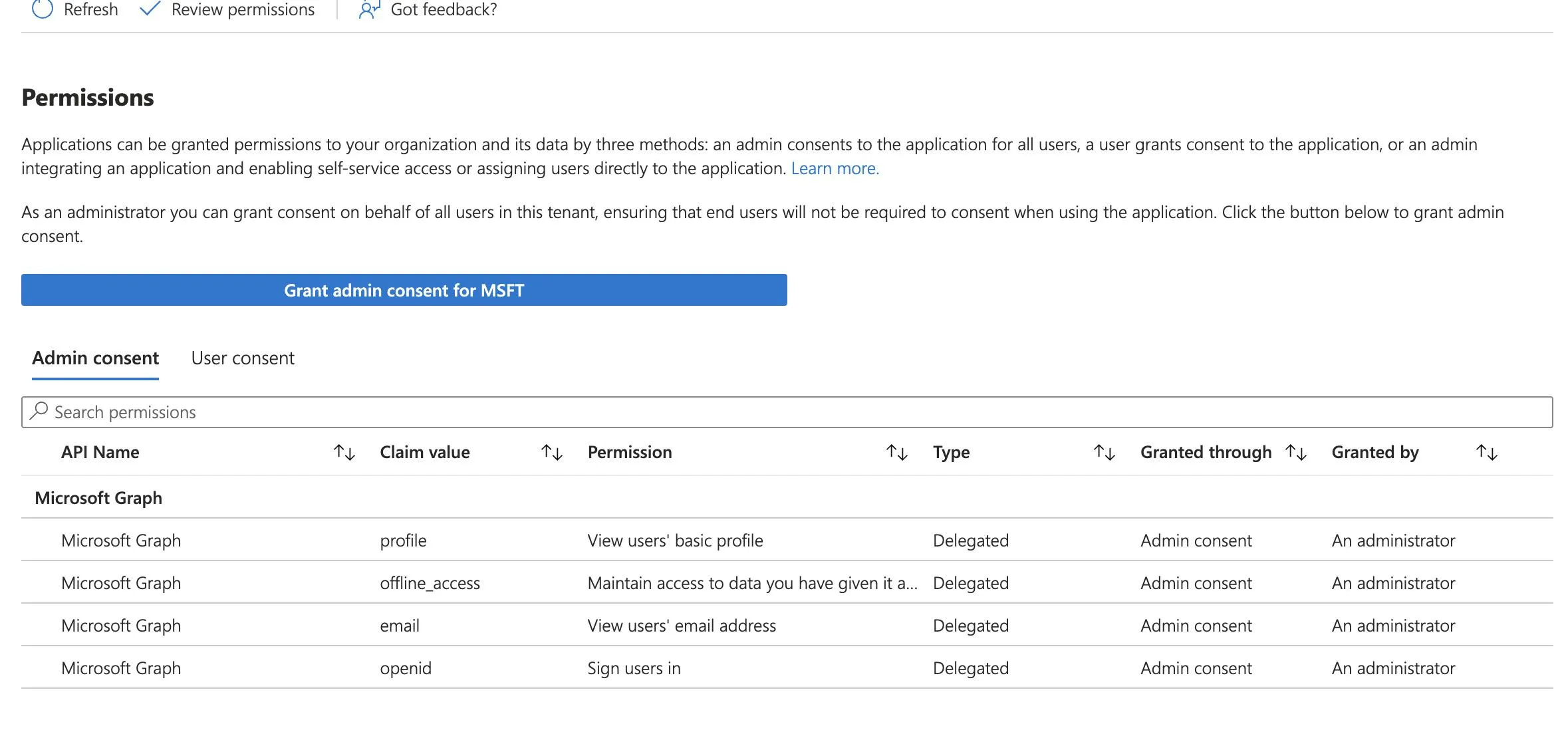
And Only when I click on Grant admin consent ( In enterprise application of tenant B Azure portal) then The missing permissions get added and the graph call works ok.
Then
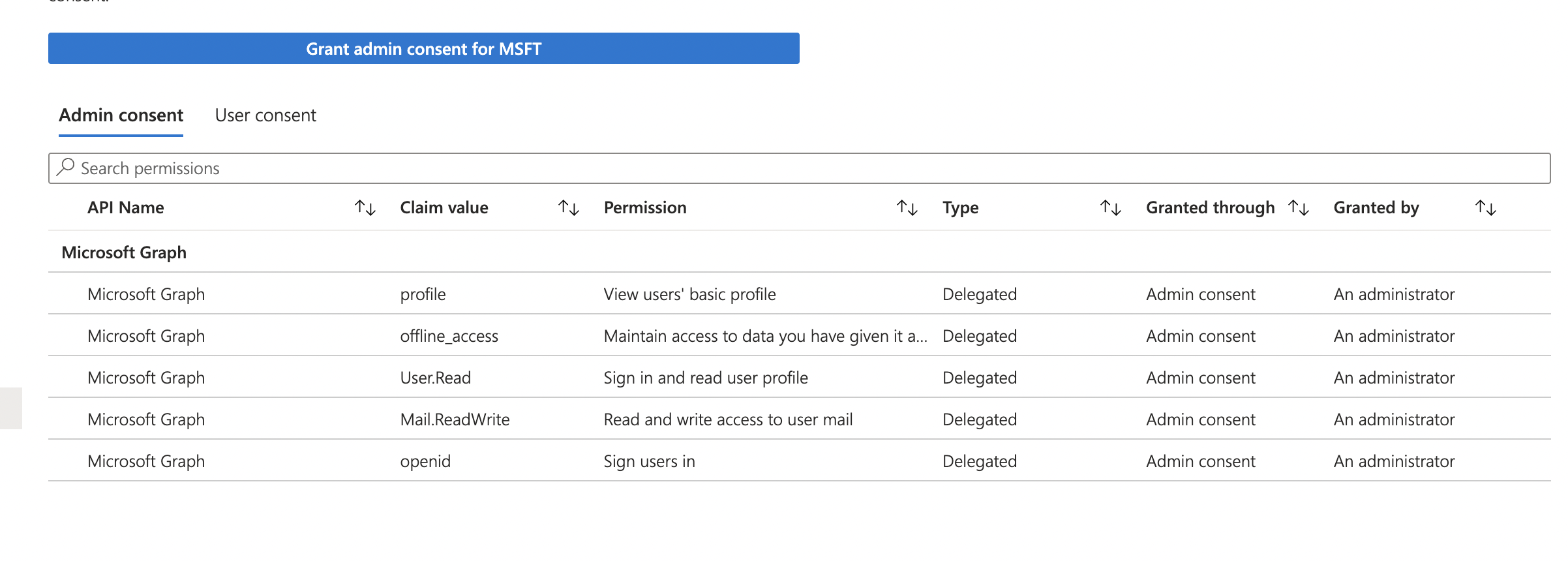
After consent :
The missing permissions are here!
What I expect as behavior is that in the consent user window user gets all the permissions. Once he grants them, the Outlook add-on should be able to call the graph on behalf of the user.
Authenticate a user with a single-sign-on token in an Outlook add-in





2
Answers
The admin for the tenant needs to provide the consent once, you can do that when installing the app. Otherwise the user will be required to to that on first login.
I created an Azure AD Multi-Tenant Application and added API permissions like below:
Now, I tried to authorize the users by using below endpoint:
The
TenantBuser got the consent screen including all the permissions like below:Code got generated:
In the
TenantBEnterprise Application, all the permissions are added in the user consent like below:Now, I generated the access token using the below parameters:
When I decoded the token, all the scopes are present:
I am able to call the Graph API successfully by using the above generated access token like below:
To resolve the error, try the below:
https://graph.microsoft.com/.defaultto get consent of all the permissions.