I’m looking to Audit VM Security Compliance given a policy definition with the chosen compliance "rules".
I currently have a VM with AzureMonitorWindowsAgent and AzurePolicyforWindows extensions installed.
I receive the following error message after assigning a custom policy definition derived from a DSC to the VM:
Compliance Details:
Reason for non-compliance
No related resources match the effect details in the policy definition. (Error code: NoComplianceReport)
Existence condition
Type
Microsoft.GuestConfiguration/guestConfigurationAssignments
Name
[concat(‘DSCPackageArtifact$pid’, uniqueString(policy().assignmentId, policy().definitionReferenceId))]
Possible solutions for this problem would be appreciated.
I previously left it for roughly 45 minutes and the error message changed to another error. However, It has not done this again.
Apologies if the names are wrong in the Policy Definition below (I have two that don’t work giving the same error. This is the smaller example, I have changed the names to match the content above)
The Policy Definition (redacted has been added to parts of the definition on purpose to post here):
{
"properties": {
"displayName": "DSCPackageArtifact_AuditIfNotExists",
"policyType": "Custom",
"mode": "All",
"description": "A few of the DSCs for testing",
"metadata": {
"properties": {
"displayName": "DSC Test NonCompliance Policy",
"policyType": "Custom",
"mode": "Indexed",
"description": "DSC Test NonCompliance Policy",
"metadata": {
"category": "Guest Configuration",
"version": "1.0.0",
"requiredProviders": [
"Microsoft.GuestConfiguration"
],
"guestConfiguration": {
"name": "DSCPackageTestNonCompliance",
"version": "1.0.0",
"contentType": "Custom",
"contentUri": "<redacted content uri with SAS token>",
"contentHash": "F5C0D40FDDCF1DBBE3C1AEF372D4B590F0D2929A220494BF6341DB8FA99A688B"
}
},
"parameters": {
"IncludeArcMachines": {
"type": "string",
"metadata": {
"displayName": "Include Arc connected machines",
"description": "By selecting this option, you agree to be charged monthly per Arc connected machine.",
"portalReview": "true"
},
"allowedValues": [
"true",
"false"
],
"defaultValue": "false"
}
},
"policyRule": {
"if": {
"anyOf": [
{
"allOf": [
{
"anyOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachineScaleSets"
}
]
},
{
"field": "tags['aks-managed-orchestrator']",
"exists": "false"
},
{
"field": "tags['aks-managed-poolName']",
"exists": "false"
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"in": [
"esri",
"incredibuild",
"MicrosoftDynamicsAX",
"MicrosoftSharepoint",
"MicrosoftVisualStudio",
"MicrosoftWindowsDesktop",
"MicrosoftWindowsServerHPCPack"
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftWindowsServer"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftSQLServer"
},
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-dsvm"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "dsvm-win*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-ads"
},
{
"field": "Microsoft.Compute/imageOffer",
"in": [
"standard-data-science-vm",
"windows-data-science-vm"
]
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "batch"
},
{
"field": "Microsoft.Compute/imageOffer",
"equals": "rendering-windows2016"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "center-for-internet-security-inc"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "cis-windows-server-201*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "pivotal"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "bosh-windows-server*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "cloud-infrastructure-services"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "ad*"
}
]
},
{
"allOf": [
{
"anyOf": [
{
"field": "Microsoft.Compute/virtualMachines/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachines/storageProfile.osDisk.osType",
"like": "Windows*"
},
{
"field": "Microsoft.Compute/VirtualMachineScaleSets/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachineScaleSets/virtualMachineProfile.storageProfile.osDisk.osType",
"like": "Windows*"
}
]
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imageSKU",
"exists": false
},
{
"allOf": [
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
}
]
}
]
}
]
}
]
},
{
"allOf": [
{
"value": "[parameters('IncludeArcMachines')]",
"equals": true
},
{
"anyOf": [
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.HybridCompute/machines"
},
{
"field": "Microsoft.HybridCompute/imageOffer",
"like": "windows*"
}
]
},
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.ConnectedVMwarevSphere/virtualMachines"
},
{
"field": "Microsoft.ConnectedVMwarevSphere/virtualMachines/osProfile.osType",
"like": "windows*"
}
]
}
]
}
]
}
]
},
"then": {
"effect": "auditIfNotExists",
"details": {
"type": "Microsoft.GuestConfiguration/guestConfigurationAssignments",
"name": "[concat('DSCPackageTestNonCompliance$pid', uniqueString(policy().assignmentId, policy().definitionReferenceId))]",
"existenceCondition": {
"field": "Microsoft.GuestConfiguration/guestConfigurationAssignments/complianceStatus",
"equals": "Compliant"
}
}
}
}
},
"name": "6c0551da-e3e9-4d16-9eb4-7e7d914de35c",
"createdBy": "6f196293-8255-4cf7-88cc-8d7b201802ee",
"createdOn": "2023-10-12T08:28:43.8359707Z",
"updatedBy": "6f196293-8255-4cf7-88cc-8d7b201802ee",
"updatedOn": "2023-10-12T08:31:05.3297191Z"
},
"parameters": {
"IncludeArcMachines": {
"type": "string",
"metadata": {
"displayName": "Include Arc connected machines",
"description": "By selecting this option, you agree to be charged monthly per Arc connected machine.",
"portalReview": "true"
},
"allowedValues": [
"true",
"false"
],
"defaultValue": "false"
}
},
"policyRule": {
"if": {
"anyOf": [
{
"allOf": [
{
"anyOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachineScaleSets"
}
]
},
{
"field": "tags['aks-managed-orchestrator']",
"exists": "false"
},
{
"field": "tags['aks-managed-poolName']",
"exists": "false"
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"in": [
"esri",
"incredibuild",
"MicrosoftDynamicsAX",
"MicrosoftSharepoint",
"MicrosoftVisualStudio",
"MicrosoftWindowsDesktop",
"MicrosoftWindowsServerHPCPack"
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftWindowsServer"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "MicrosoftSQLServer"
},
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-dsvm"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "dsvm-win*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "microsoft-ads"
},
{
"field": "Microsoft.Compute/imageOffer",
"in": [
"standard-data-science-vm",
"windows-data-science-vm"
]
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "batch"
},
{
"field": "Microsoft.Compute/imageOffer",
"equals": "rendering-windows2016"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "center-for-internet-security-inc"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "cis-windows-server-201*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "pivotal"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "bosh-windows-server*"
}
]
},
{
"allOf": [
{
"field": "Microsoft.Compute/imagePublisher",
"equals": "cloud-infrastructure-services"
},
{
"field": "Microsoft.Compute/imageOffer",
"like": "ad*"
}
]
},
{
"allOf": [
{
"anyOf": [
{
"field": "Microsoft.Compute/virtualMachines/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachines/storageProfile.osDisk.osType",
"like": "Windows*"
},
{
"field": "Microsoft.Compute/VirtualMachineScaleSets/osProfile.windowsConfiguration",
"exists": true
},
{
"field": "Microsoft.Compute/virtualMachineScaleSets/virtualMachineProfile.storageProfile.osDisk.osType",
"like": "Windows*"
}
]
},
{
"anyOf": [
{
"field": "Microsoft.Compute/imageSKU",
"exists": false
},
{
"allOf": [
{
"field": "Microsoft.Compute/imageOffer",
"notLike": "SQL2008*"
},
{
"field": "Microsoft.Compute/imageSKU",
"notLike": "2008*"
}
]
}
]
}
]
}
]
}
]
},
{
"allOf": [
{
"value": "[parameters('IncludeArcMachines')]",
"equals": true
},
{
"anyOf": [
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.HybridCompute/machines"
},
{
"field": "Microsoft.HybridCompute/imageOffer",
"like": "windows*"
}
]
},
{
"allOf": [
{
"field": "type",
"equals": "Microsoft.ConnectedVMwarevSphere/virtualMachines"
},
{
"field": "Microsoft.ConnectedVMwarevSphere/virtualMachines/osProfile.osType",
"like": "windows*"
}
]
}
]
}
]
}
]
},
"then": {
"effect": "auditIfNotExists",
"details": {
"type": "Microsoft.GuestConfiguration/guestConfigurationAssignments",
"name": "[concat('DSCPackageTestNonCompliance$pid', uniqueString(policy().assignmentId, policy().definitionReferenceId))]",
"existenceCondition": {
"field": "Microsoft.GuestConfiguration/guestConfigurationAssignments/complianceStatus",
"equals": "Compliant"
}
}
}
}
},
"id": "/subscriptions/<redacted subscription_id>/providers/Microsoft.Authorization/policyDefinitions/DSCPackageArtifact_AuditIfNotExists",
"type": "Microsoft.Authorization/policyDefinitions",
"name": "DSCPackageArtifact_AuditIfNotExists",
"systemData": {
"createdBy": "<redacted emailaddress>",
"createdByType": "User",
"createdAt": "2023-10-12T08:28:43.8134715Z",
"lastModifiedBy": "<redacted emailaddress>",
"lastModifiedByType": "User",
"lastModifiedAt": "2023-10-12T08:31:05.2747104Z"
}
}
Update: The Compliance Audit works when using a .mof file on the Desired State Configuration Management tab of the VM. However, this process has been retired for Linux (DSC Extension for Linux Retired). I’m looking for a non-retired solution.
Update 2: I have discovered that the method I am taking does not automatically create a GuestAssignment and so it looks like the NoComplianceReport is stating that It cannot find the GuestAssignment. I am trying to create it myself now to test.




2
Answers
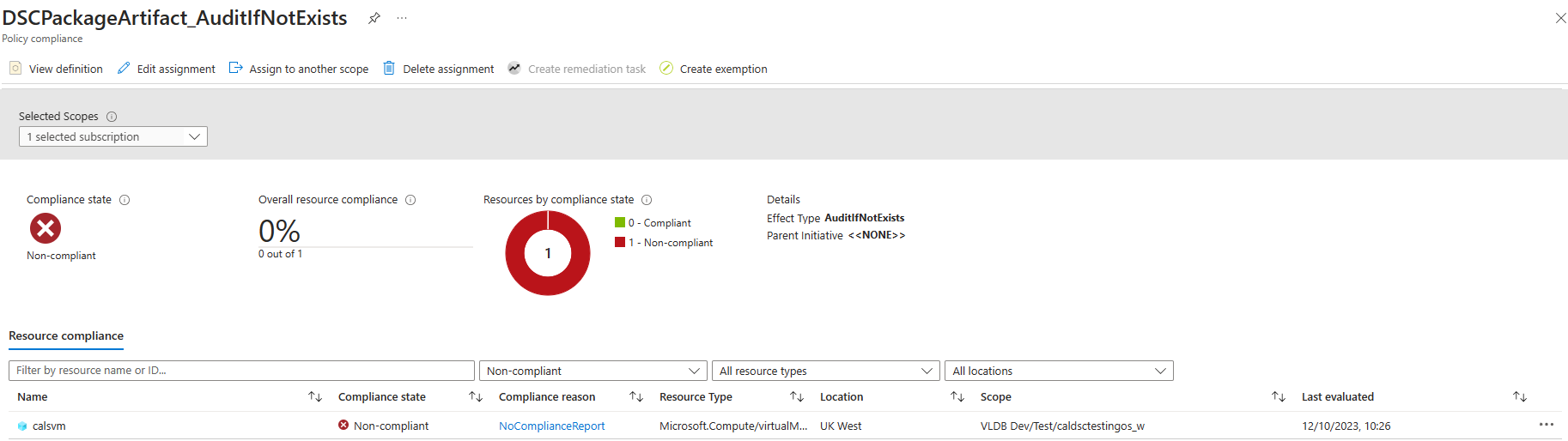
Error Message States the following:
Compliance Details:
Reason for non-compliance No related resources match the effect details in the policy definition. (Error code: NoComplianceReport)
Existence condition
Type Microsoft.GuestConfiguration/guestConfigurationAssignments Name [concat('DSCPackageArtifact$pid', uniqueString(policy().assignmentId, policy().definitionReferenceId))]
It appears that the GuestAssignment has not been automatically created as it should have.
Manually creating a GuestAssignment and changing the GuestAssignment name in the policy definition solves this issue.
Unfortunately, it is unclear why the GuestAssignment is not automatically created
To audit the security compliance of
virtual machinesandvirtual machine scale setswith the required configurations.Once the
policyis assigned to the required scope, it starts auditing the resources based on conditions, as below.