I’m trying to use Azure AD for a App-to-App authentication (grant_type: client_credentials) for calling a Rest API.
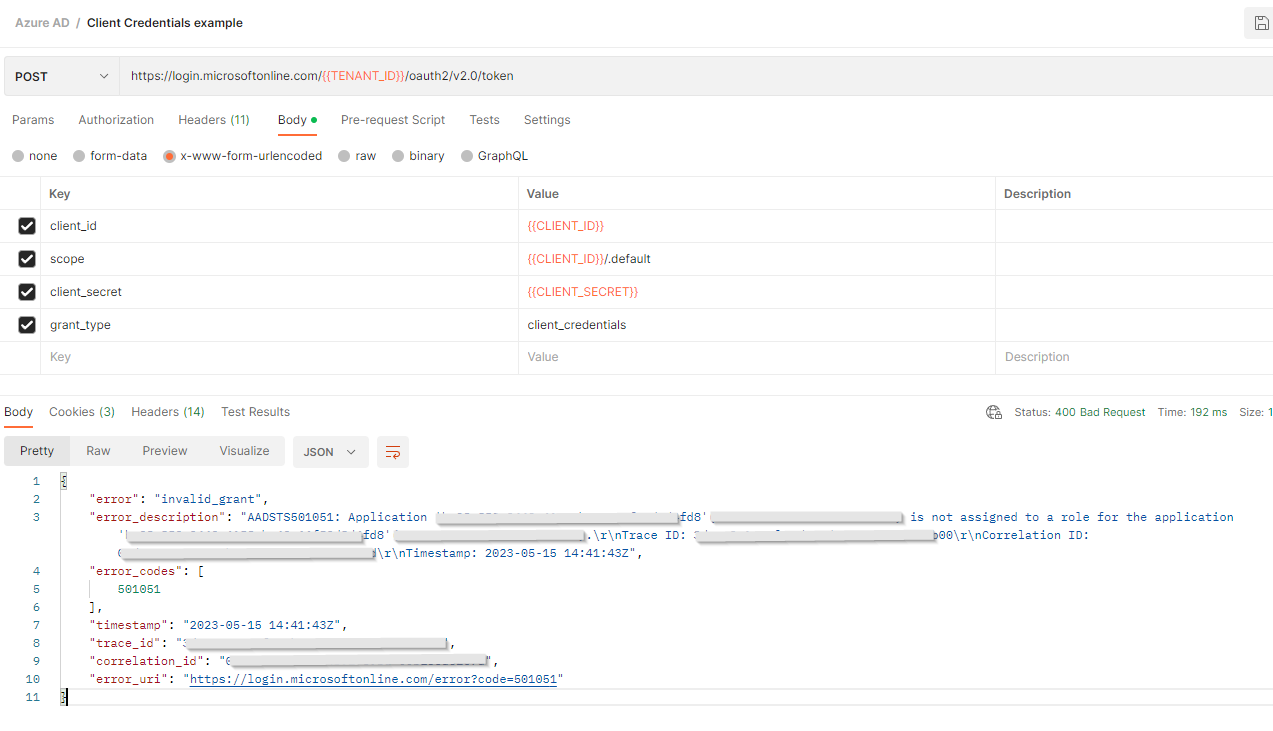
To avoid implementation issue I firstly tried with Postman with the following configuration, and got the error " Application {clientID} is not assigned to a role for the application {clientID}":
On Azure the App Registration seems to be properly configured, with a custom scope in "API permissions" and the same scope listen in "Expose an API".
What should I have to add in order to be able to call that API?
Please note that the same API works properly using IdentityServer4 with client_credentials grand type.
Thanks in advance




3
Answers
Thanks Marco, your solution works as expected. I don't need to manually edit the manifest so basically there are the 2 main configuration to do:
1-In App roles add a new role of type "Application"
2-In API permission ad a permission of type "Application permission" related to the role you've just created
In this way you are able to get an access token for that App.
TIP: In my .Net Core API I've to add this flag to the "Azure AD" configuration:
"AllowWebApiToBeAuthorizedByACL": trueSee: How to authenticate protect a backend web api for server to server communication using Azure Ad client_credentials
I created an Azure AD Application and Exposed an API like below:
And added the API permissions:
Now, when I generated the access token, I got the error like below:
The error "AADSTS501051: Application ‘ClientID'(ruktestapp) is not assigned to a role for the application ‘api://ClientID'(ruktestapp)" usually occurs if the user assignment is turned on for the Service Principal.
To resolve the error, Go to Enterprise Applications -> Select your application -> Go to properties -> Assignment required to NO and Save
Now, I generated access token successfully after few seconds applying the changes like below:
The answer from Rukmini is not entirely correct.
In the answer provided, a Delegated permissions is assigned as API permission, and the token request is with a client_credentials flow.
For client_credentials flow authentication, an Application permissions is required, not Delegated.
The issue can be fixed by keeping the "Assignment Required" on YES for security reasons (you may want to decide who, user/group or service principal, can access your application), and creating an Application permission on your App Registration.
Specifically:
That way, you can keep the Assignment required on YES and use both client_credential and other flows.
For other flows, you need to add also the Delegated permissions.