My question would have been redundant if Enable azure app service authentication and create app registration in azure cli took it all the way to the answer. But it stops at creation of a bare app registration.
So, here I have run the following commands:
az webapp auth update -n my-webapp -g my-rg --enabled true --action RedirectToLoginPage --enable-token-store false
az ad app create --display-name my-app-reg
But how to proceed then?
EDIT 1
First – my Azure CLI version:
mark@L-R910LPKW:~$ az version
{
"azure-cli": "2.55.0",
"azure-cli-core": "2.55.0",
"azure-cli-telemetry": "1.1.0",
"extensions": {
"aks-preview": "0.5.173",
"application-insights": "1.0.0",
"authV2": "0.1.3",
"azure-devops": "0.26.0",
"storage-preview": "1.0.0b1",
"virtual-wan": "0.3.0"
}
}
mark@L-R910LPKW:~$
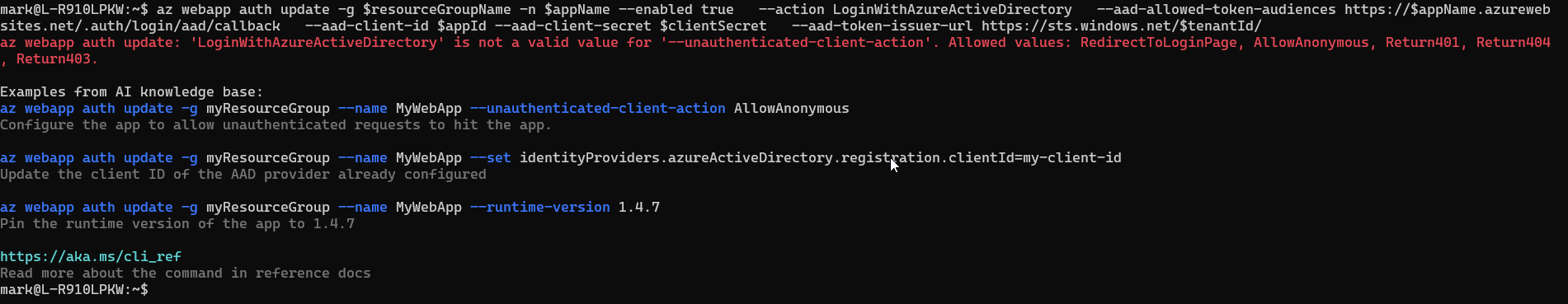
Now trying to create the App Registration:
Take 1
mark@L-R910LPKW:~$ az webapp auth update -g $resourceGroupName -n $appName --enabled true --action LoginWithAzureActiveDirectory --aad-allowed-token-audiences https://$appName.azurewebsites.net/.auth/login/aad/callback --aad-client-id $appId --aad-client-secret $clientSecret --aad-token-issuer-url https://sts.windows.net/$tenantId/
az webapp auth update: 'LoginWithAzureActiveDirectory' is not a valid value for '--unauthenticated-client-action'. Allowed values: RedirectToLoginPage, AllowAnonymous, Return401, Return404, Return403.
Examples from AI knowledge base:
az webapp auth update -g myResourceGroup --name MyWebApp --unauthenticated-client-action AllowAnonymous
Configure the app to allow unauthenticated requests to hit the app.
az webapp auth update -g myResourceGroup --name MyWebApp --set identityProviders.azureActiveDirectory.registration.clientId=my-client-id
Update the client ID of the AAD provider already configured
az webapp auth update -g myResourceGroup --name MyWebApp --runtime-version 1.4.7
Pin the runtime version of the app to 1.4.7
https://aka.ms/cli_ref
Read more about the command in reference docs
mark@L-R910LPKW:~$
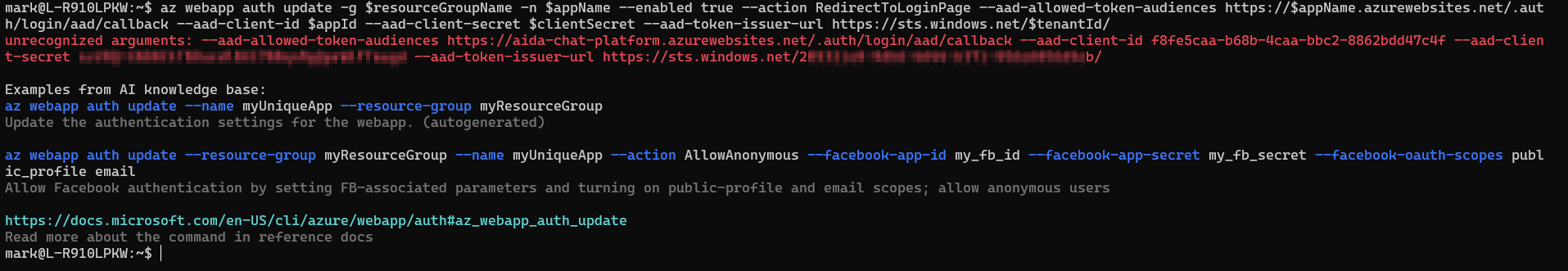
Take 2
mark@L-R910LPKW:~$ az webapp auth update -g $resourceGroupName -n $appName --enabled true --action RedirectToLoginPage --aad-allowed-token-audiences https://$appName.azurewebsites.net/.auth/login/aad/callback --aad-client-id $appId --aad-client-secret $clientSecret --aad-token-issuer-url https://sts.windows.net/$tenantId/
unrecognized arguments: --aad-allowed-token-audiences https://aida-chat-platform.azurewebsites.net/.auth/login/aad/callback --aad-client-id f8fe5caa-b68b-4caa-bbc2-8862bdd47c4f --aad-client-secret *** --aad-token-issuer-url https://sts.windows.net/2...b/
Examples from AI knowledge base:
az webapp auth update --name myUniqueApp --resource-group myResourceGroup
Update the authentication settings for the webapp. (autogenerated)
az webapp auth update --resource-group myResourceGroup --name myUniqueApp --action AllowAnonymous --facebook-app-id my_fb_id --facebook-app-secret my_fb_secret --facebook-oauth-scopes public_profile email
Allow Facebook authentication by setting FB-associated parameters and turning on public-profile and email scopes; allow anonymous users
https://docs.microsoft.com/en-US/cli/azure/webapp/auth#az_webapp_auth_update
Read more about the command in reference docs
mark@L-R910LPKW:~$
EDIT 2
I have positive progress thanks to https://stackoverflow.com/a/77911481/80002. My issue was that while trying all kinds of things I enabled the authV2 Azure CLI extension and that removed the LoginWithAzureActiveDirectory action from the list of actions supported by the az webapp auth update command. Once I removed that extension (az extension remove) I successfully ran the command proposed in that answer.
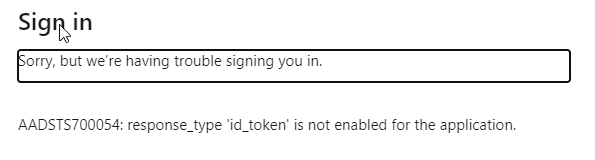
And it opens the SSO login dialog as expected, but trying to login results in this:
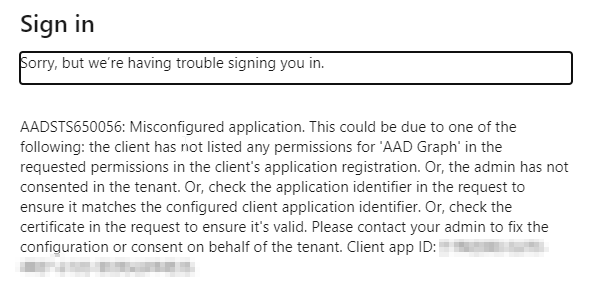
EDIT 3
So I ran the following to try and resolve the issue:
az ad app update --id $appId --enable-id-token-issuance true

 Question posted in
Question posted in 

2
Answers
I was able to make it work by following these steps:
az webapp up --runtime PYTHON:3.9 --sku B1 --logsto create the App Service itself. Verify it works.az webapp auth config-version upgrade --id {web app id}az extension add -n authV2az ad app create --display-name {App Name} --enable-id-token-issuance true --web-redirect-uris https://{web app name}.azurewebsites.net/.auth/login/aad/callback --required-resource-accesses @manifest.json(see manifest.json below). Notice the App RegistrationappId.az ad app credential reset --id {appId}- notice the password.az webapp auth update --ids {Web App Id} --enabled true --action RedirectToLoginPageaz webapp auth microsoft update --ids {Web App Id} --client-id {appId} --client-secret {app secret} --tenant-id {Tenant Id}manifest.json (I found it in https://stackoverflow.com/a/69719989)
Now let us run the steps from scratch:
/subscriptions/0...7/resourceGroups/ee742f99-0a52-4c3a-a3e0-a3e4bd961a1c_rg_0877/providers/Microsoft.Web/sites/red-water-476d8199b06644b99e3f30c29cff99d7https://red-water-476d8199b06644b99e3f30c29cff99d7.azurewebsites.net/Now let us enable authentication:
And it works at least for me.
One thing that bothers me is that the Authentication page of the App Service shows a rather nasty warning:
Other than that it seems to work.
I have one App Service named
demowebapp31without any authentication configured like this:You can make use of below CLI script that creates azure ad app registration with client secret and adds authentication to App service:
Response:
To confirm that, I checked the same in Portal where authentication is added successfully to App service like this:
References:
az webapp auth | Microsoft
Manage AuthN/AuthZ API versions – Azure App Service | Microsoft