I am using an Azure DevOps pipeline where i use different Service Connections for connecting to Azure ARM and Docker. When I create a connection a corresponding service principal gets created in Azure.
I created a connection for Azure ARM
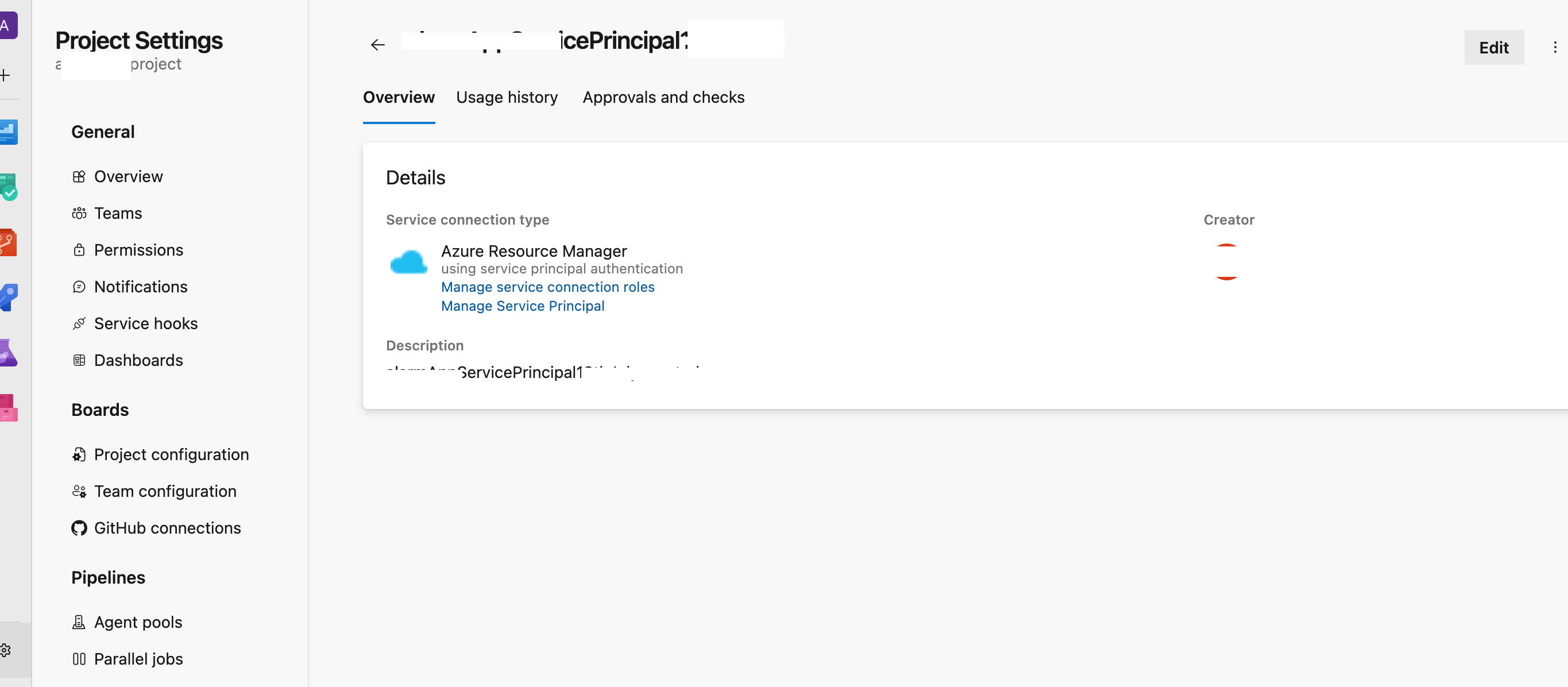
I want to assign some roles to this service connection in azure. I click on the Manage Service Principal link in the Overview page of Service Connection.
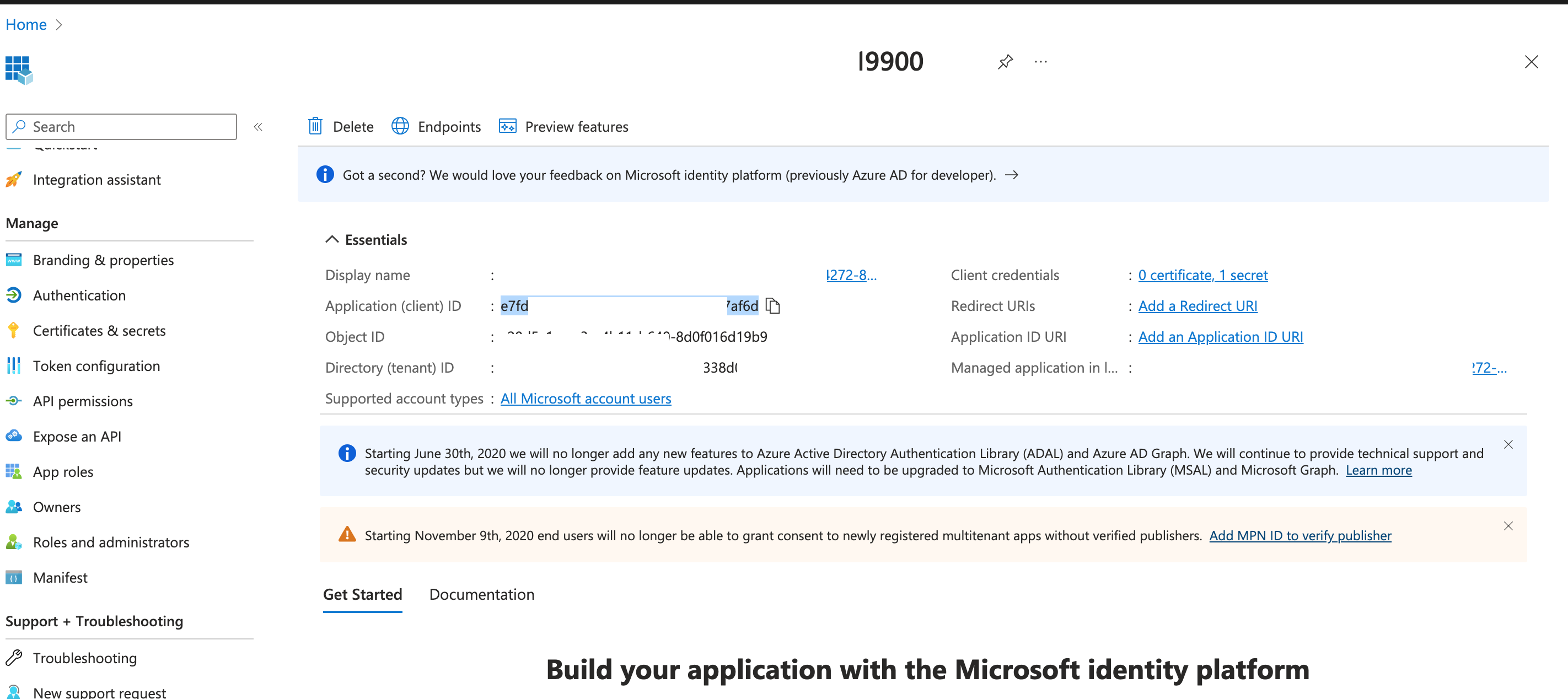
It leads me to the Azure portal Service Principal page.
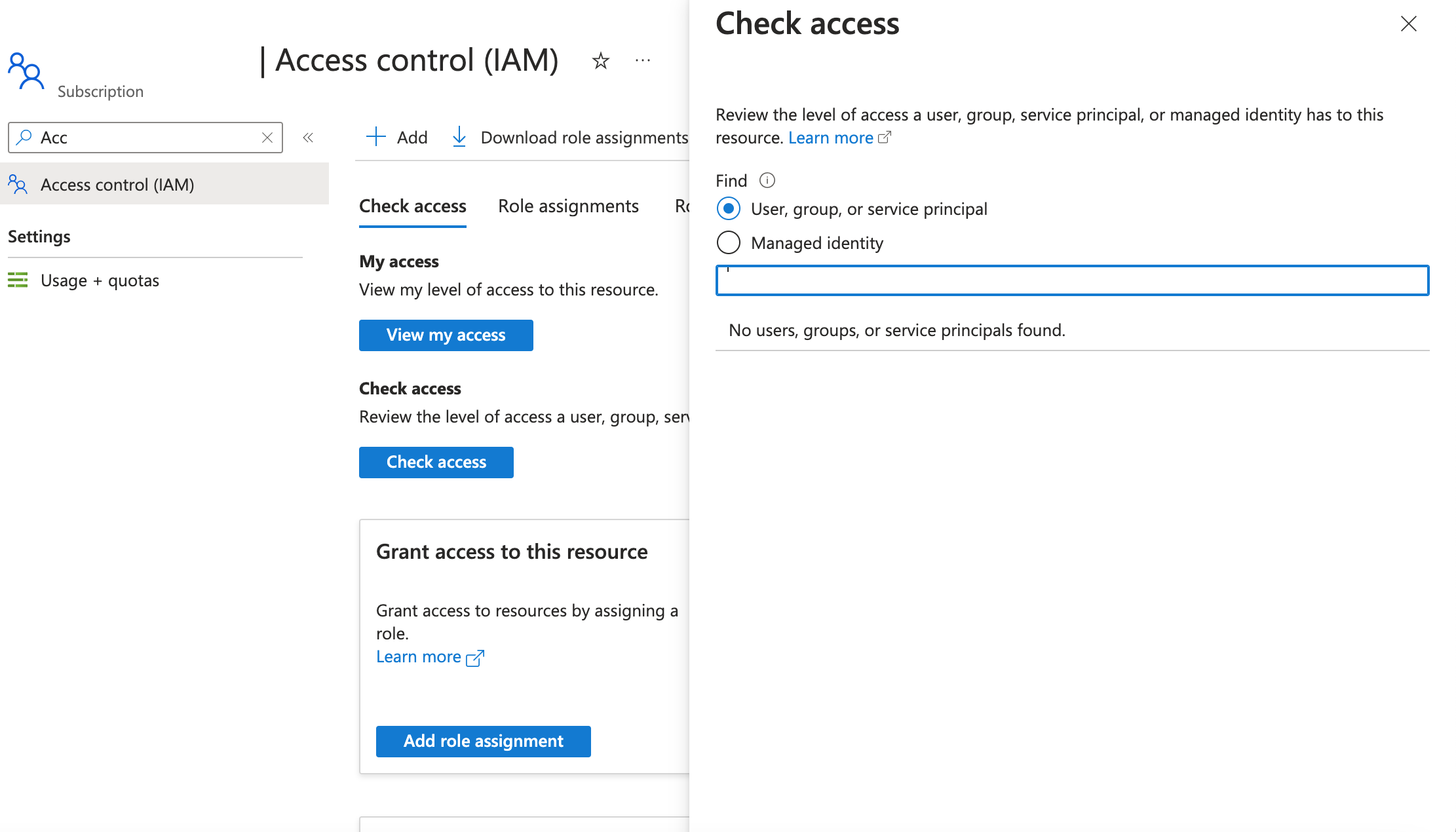
I copy the ClientId from that page and go the Access Control screen and for assigning the access, i enter the ClientId with the User,group or service principal selected:
I get no results found, for the client id.
Can anyone help me understand this ? Thanks




2
Answers
Please copy
display namefrom the Azure portal Service Principal page and use this for filtering in the assigning permission dialog.I concur with the Krzysztof Madej that filtering by display name can be used to assign permission. However, it can be challenging to locate the necessary service account under IAM access if you have numerous service principles with the same name. Unfortunately, it is not feasible to locate the service principal using the object Id and Client Id. Maintaining distinctive names for service principals is always a good idea. You can also rename the existing service principal.
I followed the steps below to help identifying the right service principal.
Step-1: Go to the right serice principal.
https://i.imgur.com/dip7eRA.png
Step-2: Rename the service principal by navigating to the Brandings & properties as shown in below image

Step-3: Now go to the IAM and search the service principal with Display Name.
