I’m using Azure Active Directory B2C for external authorization by Azure.
Everything was working fine until Friday 19 when suddenly my backend could not respond because it couldn’t receive configuration info from a static link.
The interesting thing, this link is fully workable, it opens json file when go by this URL in the browser, but my backend cannot access it.
The temporary decision was to load this file to the s3 bucket on AWS to get its public URL and change the link to this file in my application configuration. But this decision is ugly, and I want to figure out what the problem is.
Stack: .Net Framework 4.6.2.
Link to configuration file in my project settings:
<add key="ida:AadInstance" value="https://xxx.b2clogin.com/{0}/v2.0/.well-known/openid-configuration?p={1}" />




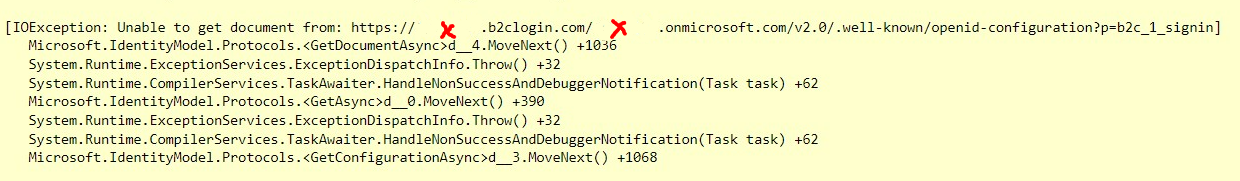
2
Answers
Okay, the problem was in the TLS version. My application used the TLS 1.1 version by default. I think Azure silently deprecated TLS 1.1 version, and all requests are skipped with status code 426 Upgrade required.
The solution was to change the TLS version to 1.2 in my project.
The following code resolved my problem:
Yes for the Dotnet framework later than 4.6.x must have the upgraded tls version.
I could successfully bypass the error by using tls version 1.2
System.Net.ServicePointManager.SecurityProtocol = System.Net.SecurityProtocolType.Tls12;Check the following:
Startup.cs:
}
Appsettings.json
Ensure the latest frameworks are upgraded with latest patches and also check for the network connectivity.
Then the program can be run successfully with azure ad b2c