I installed kubernetes in Hetner based on the repository.
I am using godaddy as DNS management
I have install cert manager in the cluster. I took it from here.
kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.12.0/cert-manager.yaml
Load balancer:
apiVersion: v1
kind: Service
metadata:
name: example-lb
annotations:
load-balancer.hetzner.cloud/location: hel1
spec:
selector:
app: example
ports:
- port: 80
targetPort: 5678
type: LoadBalancer
Deployment:
apiVersion: apps/v1
kind: Deployment
metadata:
name: example
spec:
selector:
matchLabels:
app: example
replicas: 1
template:
metadata:
labels:
app: example
spec:
containers:
- name: echo1
image: hashicorp/http-echo
args:
- "-text=echo1"
ports:
- containerPort: 5678
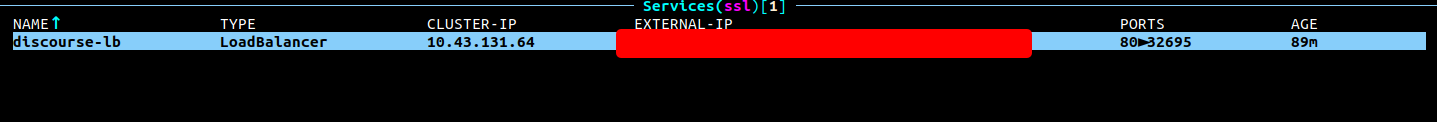
Load balancer got 32695 port
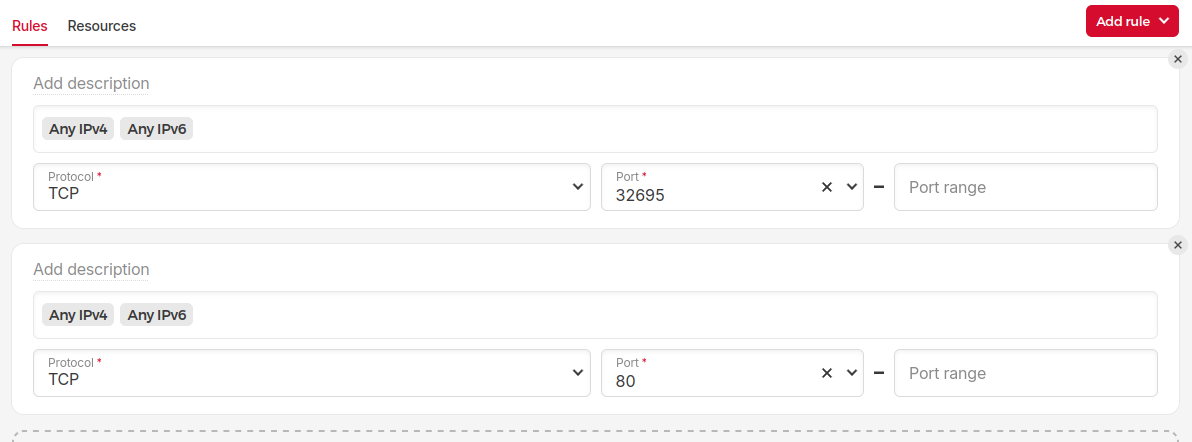
I open firewall for 32695 and 80 ports.
I made an A record to connect my load balancer with subdomain.
I can connect to my pod through the http URL.
ClusterIssuer manifest:
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
namespace: cert-manager
spec:
acme:
email: [email protected]
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-issuer-account-key
solvers:
- http01:
ingress:
class: nginx
Certificate manifest
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: secure-homekube-io
namespace: default
spec:
secretName: secure-homekube-io-tls
duration: 2160h # 90d
renewBefore: 360h # 15d
subject:
organizations:
- my-org
isCA: false
privateKey:
algorithm: RSA
encoding: PKCS1
size: 2048
usages:
- server auth
- client auth
dnsNames:
- my.sub.domain
issuerRef:
name: letsencrypt-prod
kind: ClusterIssuer
group: cert-manager.io
The question is why certificate has false status?
Update
Describe Challenges:
Waiting for HTTP-01 challenge propagation: did not get expected response when querying endpoint, expected "some.sensitive.data." but got: echo1

 Question posted in
Question posted in 


2
Answers
value file:
Connect load-balancer public IP to your DNS
apply Cluster issuer:
7 Ingress, service and deployment for test
i think the issue might be in one or more of the following:
1- Well, I have no experience with hetzner cloud, but as per the link you provided, the annotations of load-balancer requires two annotations. however, you added only one of them
if your case requires communication with public IP, then adjust your firewall and add yours.
2- in the cluster issuer manifest, you configured the solver to http01 not dns i think the correct one is:
then update the certificate and make sure that your subdomain is configured correctly and the a record exists in godaddy and routes to the desired IP.