I am trying to deploy container app from classic release pipeline.
I need to attach environment variables to container app and those environment value has to fetch from azure key vault. I have created azure key vault and authorised it in release pipeline.
Below are my two tasks in Ubuntu agent job of release pipeline.
- Azure key vault
- Azure container app deploy
In the second task of azure container app deploy, I am passing environment variables as below,
Server-id=$(server-id)
This $(server-id) is the secret name in azure key vault and this value has to fetch from vault.
During the pipeline job, secrets are downloaded successfully and container app also deployed with environment variables I mentioned.
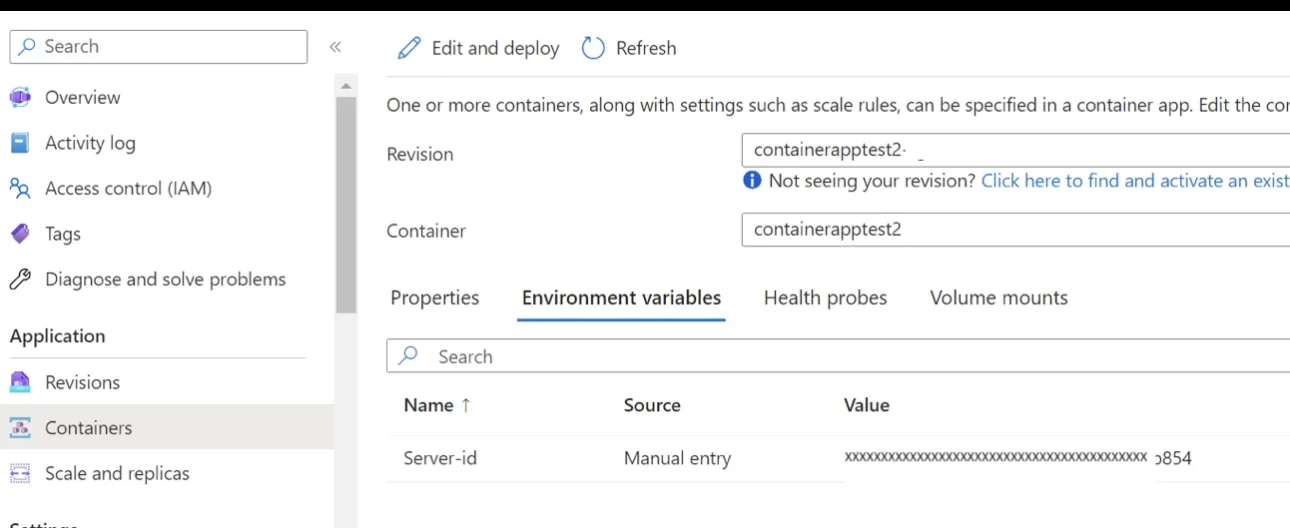
After this, if I go to container app console, under environment variable I can clearly see the variable value of server-id.
In below image, container app environment variable are clearly seen.(for sharing purpose I made masked manually in the image )
Also I tried other options environment variables as
1.Server-id=$(@Microsoft.Keyvault(SecureUri=https://test.azure.net/secrets/server-id))
2. Server-id=secretref:$(@Microsoft.Keyvault(SecureUri=https://test.azure.net/secrets/server-id))
Both options didn’t work as expected.
I want to use environment variables from azure key vault where it’s environment values should not visible under container app environment details.
Other options which I looked into secrets creation under container app in azure but unable to do this azure classic release pipeline.



2
Answers
This is not possible. All details in environment variables are always visible in portal. For this purpose you should use secrets. And you can use azure cli to set secret
Please notice the format used for secrets:
you can implement this using Variable groups per environment and linking it to secrets from an Azure vault. link for more info
https://learn.microsoft.com/en-us/azure/devops/pipelines/release/azure-key-vault?view=azure-devops&tabs=yaml