I have configured openvpn (OpenVPN 2.4.12 x86_64-pc-linux-gnu) on my ubuntu server.
My openvpn client (using openwrt router) is able to setup a vpn with my openvpn server.
The problem is that I cannot access my client private network (192.168.8.0/24) from the openvpn server.
openvpn server: IP 192.168.2.12 (tun0 10.8.0.1)
openvpn client: IP 192.168.8.1 (tun0 10.8.0.4)
From my openvpn server I can ping to 10.8.0.4 but not to 192.168.8.1
Using tcpdump -i tun0 on my openvpn server I see that when I ping 192.168.8.1 that there is no ping trafic seen on my tun0 interface. So it is not routing 192.168.8.1 to my tunnel. This is also confirmed by traceroute which shows that it sends 192.168.8.1 to my router (192.168.2.1):
root@nuc2:~# traceroute 192.168.8.1
traceroute to 192.168.8.1 (192.168.8.1), 64 hops max
1 192.168.2.1 0,210ms 0,226ms *
2 * * *
FYI traceroute from my openvpn server to VPN ip address of my vpn client is giving the following:
traceroute to 10.8.0.4 (10.8.0.4), 64 hops max
1 10.8.0.4 7,268ms 7,170ms 6,670ms
root@nuc2:~#
This is my /etc/openvpn/server/server.conf file:
local 192.168.2.12
port 1194
proto udp
dev tun
ca ca.crt
cert server.crt
key server.key
dh dh.pem
auth SHA512
tls-crypt tc.key
topology subnet
server 10.8.0.0 255.255.255.0
route 192.168.8.0 255.255.255.0
push "route 192.168.2.0 255.255.255.0"
push "redirect-gateway def1 bypass-dhcp"
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 192.168.2.1"
push "dhcp-option DOMAIN lan"
push "dhcp-option DOMAIN-SEARCH lan"
keepalive 10 120
cipher AES-256-CBC
user nobody
group nogroup
persist-key
persist-tun
verb 3
crl-verify crl.pem
explicit-exit-notify
client-config-dir /etc/openvpn/client
And I have also created a file /etc/openvpn/client/gl-inet.conf with following contents which I thought would assure routing of subnet 192.168.8.0/24 traffic on my openvpn server to the VPN:
iroute 192.168.8.0 255.255.255.0
Note that in my log files (using command tail -f /var/log/syslog | grep -i vpn) on the openvpn server I don’t see any indication that this file (gl-inet.conf) is read or that this route is processed. So maybe the name gl-inet.conf is not correct or something extra needs to be done to assure that that client configuration file is processed.
FYI an extract of tail -f /var/log/syslog | grep -i vpn:
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 TLS: Initial packet from [AF_INET]192.168.2.1:44409, sid=577f0ed8 416e3b2c
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 VERIFY OK: depth=1, CN=ChangeMe
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 VERIFY OK: depth=0, CN=gl-inet
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_VER=2.5.2
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_PLAT=linux
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_PROTO=6
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_NCP=2
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:AES-256-CBC
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_LZ4=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_LZ4v2=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_LZO_STUB=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_COMP_STUB=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_COMP_STUBv2=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 peer info: IV_TCPNL=1
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 2048 bit RSA
Jan 21 10:38:23 nuc2 openvpn[5147]: 192.168.2.1:44409 [gl-inet] Peer Connection Initiated with [AF_INET]192.168.2.1:44409
Jan 21 10:38:23 nuc2 openvpn[5147]: MULTI: new connection by client 'gl-inet' will cause previous active sessions by this client to be dropped. Remember to use the --duplicate-cn option if you want multiple clients using the same certificate or username to concurrently connect.
Jan 21 10:38:23 nuc2 openvpn[5147]: MULTI_sva: pool returned IPv4=10.8.0.4, IPv6=(Not enabled)
Jan 21 10:38:23 nuc2 openvpn[5147]: MULTI: Learn: 10.8.0.4 -> gl-inet/192.168.2.1:44409
Jan 21 10:38:23 nuc2 openvpn[5147]: MULTI: primary virtual IP for gl-inet/192.168.2.1:44409: 10.8.0.4
Jan 21 10:38:25 nuc2 openvpn[5147]: gl-inet/192.168.2.1:44409 PUSH: Received control message: 'PUSH_REQUEST'
Jan 21 10:38:25 nuc2 openvpn[5147]: gl-inet/192.168.2.1:44409 SENT CONTROL [gl-inet]: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 192.168.2.1,dhcp-option DOMAIN lan,dhcp-option DOMAIN-SEARCH lan,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.4 255.255.255.0,peer-id 0,cipher AES-256-GCM' (status=1)
Jan 21 10:38:25 nuc2 openvpn[5147]: gl-inet/192.168.2.1:44409 Data Channel: using negotiated cipher 'AES-256-GCM'
Jan 21 10:38:25 nuc2 openvpn[5147]: gl-inet/192.168.2.1:44409 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Jan 21 10:38:25 nuc2 openvpn[5147]: gl-inet/192.168.2.1:44409 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
I have also defined a static route to my openvpn server on the router of my openvpn server network.




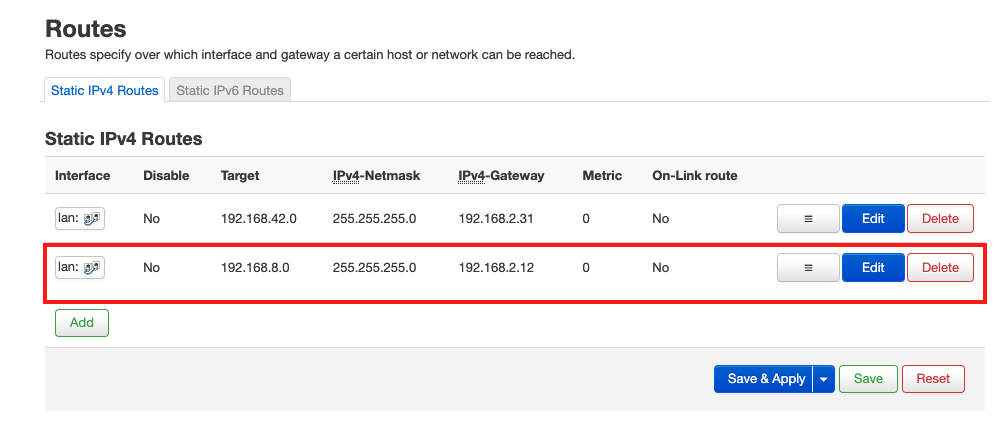
2
Answers
The client config file should be named without the
.confsuffix. So in my case it should be/etc/openvpn/client/gl-inet.The other thing is that I had to reboot my openvpn server to get it working properly (so some of the settings only got in effect after reboot - restarting openvpn server was not sufficient).
After rebooting my openvpn server and setting up a vpn connection from my openvpn client and running command
ip routeon my openvpn server I get the following:The last line seem to assure the routing to my client subnet.
Have you tried to define the gateway like this:
route 192.168.8.0 255.255.255.0 10.8.0.1
It looks like otherwise it just takes the default gateway of the server.
EDIT: There is an "l" missing in the first line of the config. ocal -> local